Pig Butchering Scam: From Tinder and TikTok to WhatsApp and Telegram, How Scammers Are Stealing Millions in a Long Con

In part one of a two-part series on Pig butchering, we detail the pervasive scam that has impacted thousands of victims around the world, resulting in the loss of hundreds of millions of dollars. This blog highlights the who and the how of pig butchering scams, and details the pig butchering playbook.
Background
Pig butchering — a translation of the Chinese phrase “Shāzhūpán” (Sha Zhu Pan) used to describe a type of financial scam — has enabled scammers to steal hundreds of millions of dollars. That’s according to the FBI’s 2021 Internet Crime Report, which pegged losses at over $429 million based on reports from thousands of people in the United States. However, pig butchering knows no geographic bounds, and there are also thousands of victims of these scams globally. Pig butchering scams occur across a variety of social media and messaging platforms as well as on most dating apps. It is likely that the true cost of pig butchering is much higher than reported, especially because pig butchering scams overlap between romance and investment scams. It is my assessment that pig butchers are, in a way, everywhere, all at once, and the true extent of their operations is not fully understood.
This is the first part of a two-part blog series that details my firsthand research into pig butchering scams from the end of 2022 into early 2024. This post offers a primer on what pig butchering is and how these scammers target users on various platforms – from social media to dating apps. In the second part of this series, I will detail the types of financial fraud the scammers use to steal money from their victims, which includes falsified cryptocurrency investments.
Table of Contents
- Who are pig butchers?
- Who are the pigs?
- What does pig butchering mean?
- Does pig butchering target a specific audience?
- How do pig butchers contact potential victims?
- Why do pig butchers want to move off platform to WhatsApp, Telegram or SMS?
- Are the same people behind both the social media and dating app profiles and the messaging apps?
- Are all of the images on these social media and dating app profiles fake?
- But the person had a Facebook and Instagram account. Are those fake, too?
- Have you seen artificial intelligence (AI) generated images used on these fake profiles?
- Where are these pig butchering scammers based out of?
- What is in the pig butcher's playbook?
Who are pig butchers?
Pig butchers are scammers operating a network of fake accounts across a plethora of social media, messaging and dating applications, including:
- Telegram
- TikTok
- X (formerly known as Twitter)
- Tinder
- Bumble
- Hinge
The list above is not intended to be exhaustive, but rather a sampling of applications where I’ve interacted with confirmed pig butchers.
Who are the pigs?
The “pig” in pig butchering is a reference to the individual victims targeted by the pig butchers.
What does pig butchering mean?
The phrase “pig butchering” highlights how such scammers “fatten up” their victims, whether through prolonged romantic conversations or by convincing victims that they stand to reap significant profits from investment opportunities. In either case, the goal is the financial “slaughter” of the “pigs” by persuading them to hand over large sums of fiat currency or cryptocurrency.
Does pig butchering target a specific audience?
No, unlike the traditional adult-dating scams I’ve previously researched, pig butchering does not target any particular gender or ethnicity.
How do pig butchers contact potential victims?
It depends on the application they’re using. For example, messaging applications like WhatsApp or Telegram rely on a user’s contacts to help build out their network or community. Therefore, the pig butchering scammers will rely on a hook whereby they send a message to a potential victim in the hopes that they will reply.
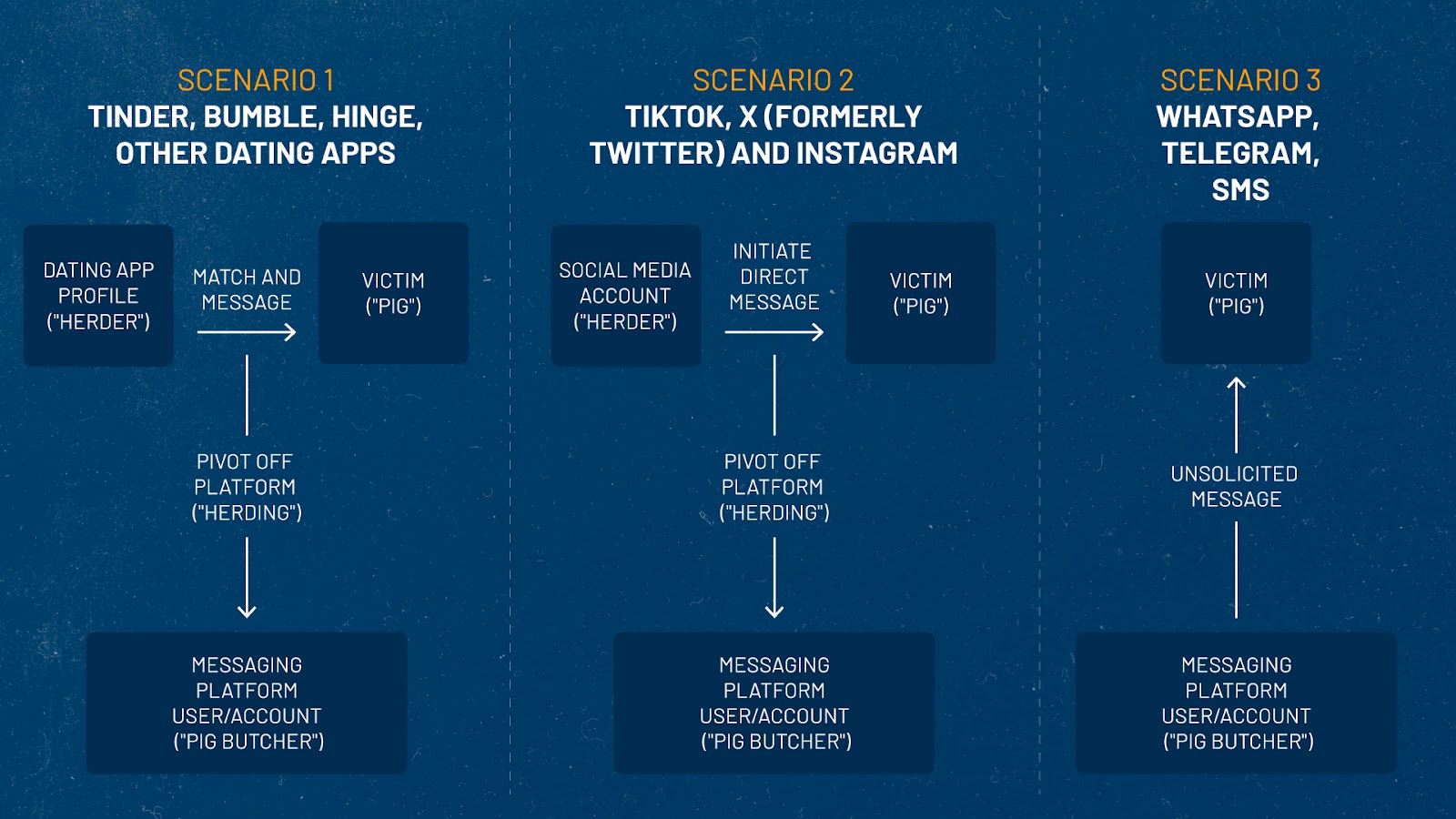
Below are some examples of how pig butchering scams begin on the various platforms:
WhatsApp and Telegram
Users of WhatsApp and Telegram, or short message service (SMS) messages are likely to receive a type of “cold-call” (or unsolicited message) using a wrong name, or outright asking the potential victim if they are someone else and asking to verify if their number has changed.
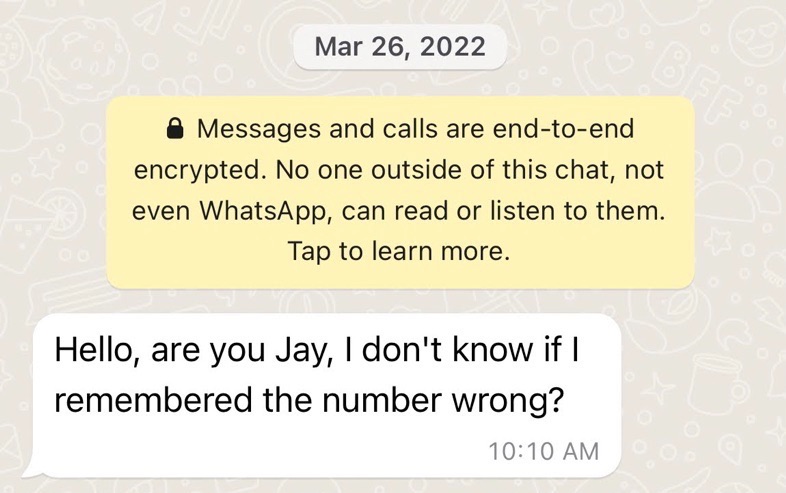
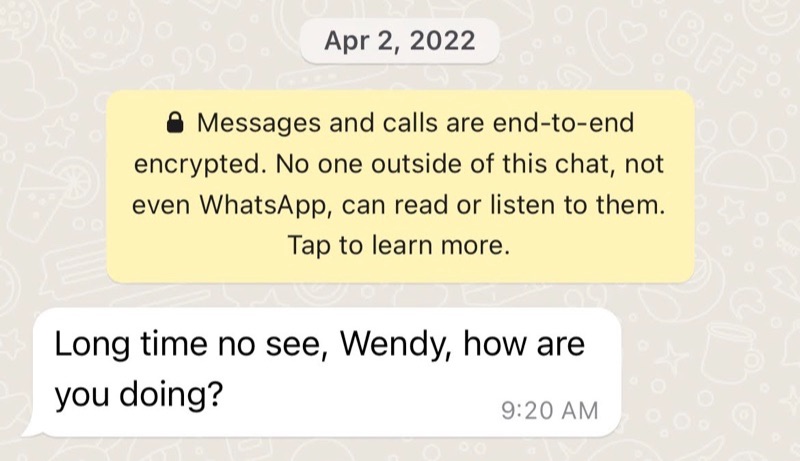
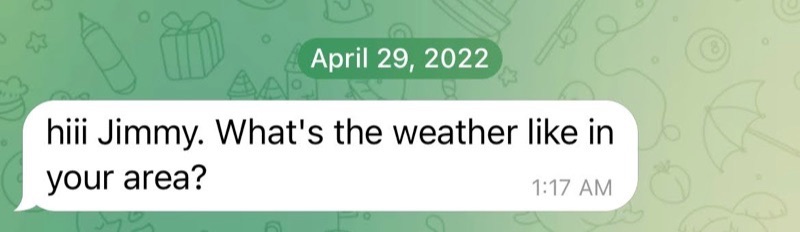
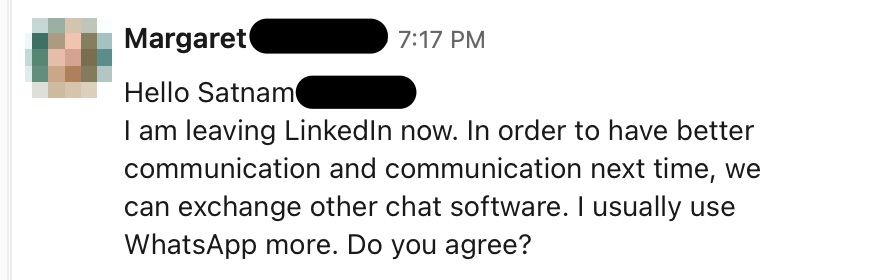
TikTok, Twitter, LinkedIn and other social media
Social media users can expect to receive similar cold call messages, although the pig butchers on these platforms tend to be more definitive in their intentions to seek a deeper, more intimate conversation with the potential victim. Pig butchers on these platforms will often ask users to move the conversation onto a platform like WhatsApp, Telegram or SMS.
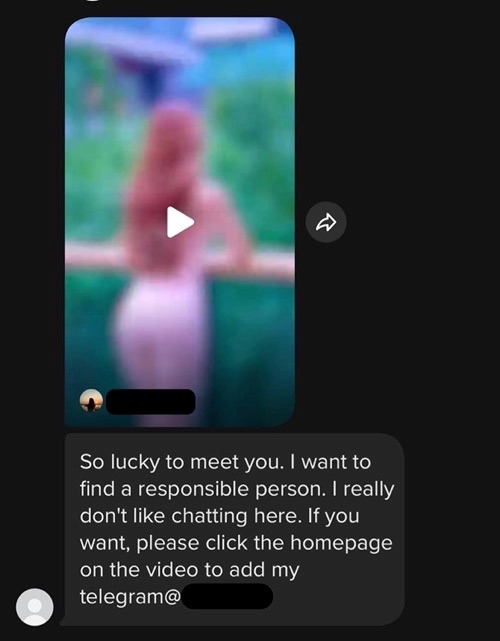
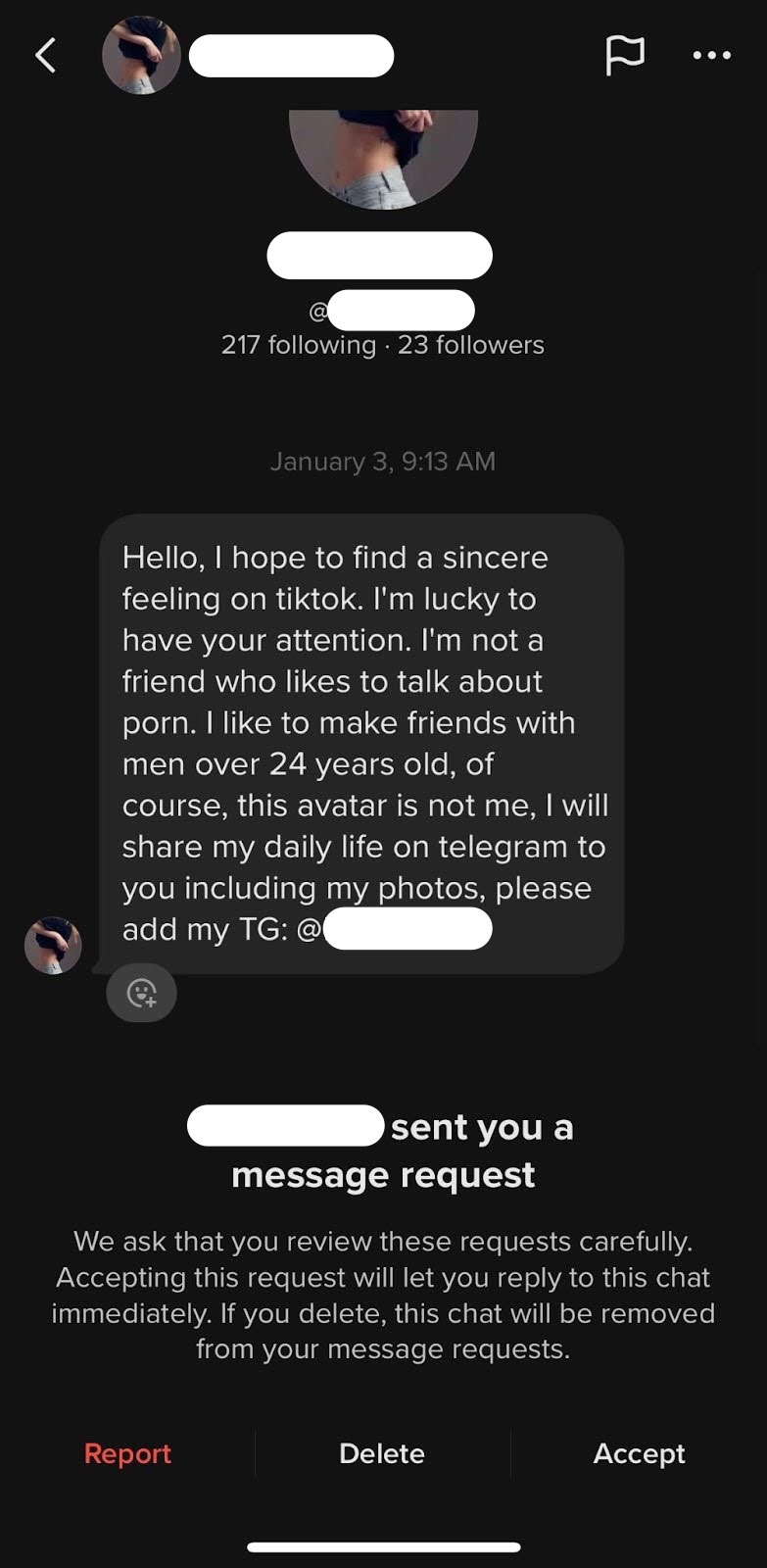
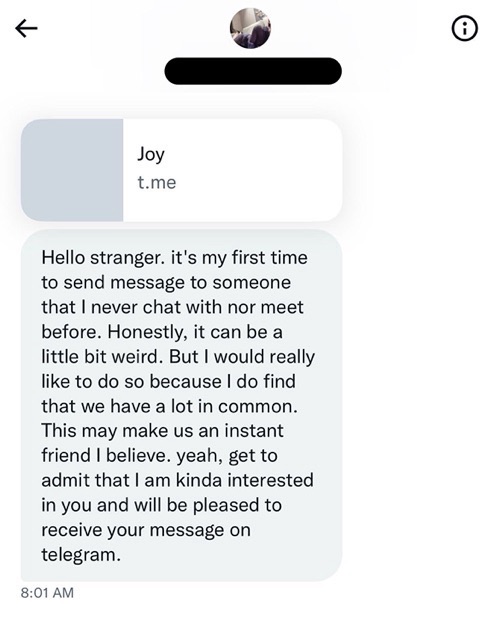
Tinder, Bumble and other dating applications
Unlike messaging and social media platforms, dating applications require users to match before they can begin sending messages to one another. While the pig butchers could put information in their profiles to entice users to message them off platform, that’s likely to set off alarm bells with app moderators and could lead to their dating app profiles being removed. Therefore, they typically wait to match with users and begin a conversation before enticing them to pivot to another platform.
I encountered pig butchering related profiles on a variety of dating apps, including Tinder, Bumble and Hinge.
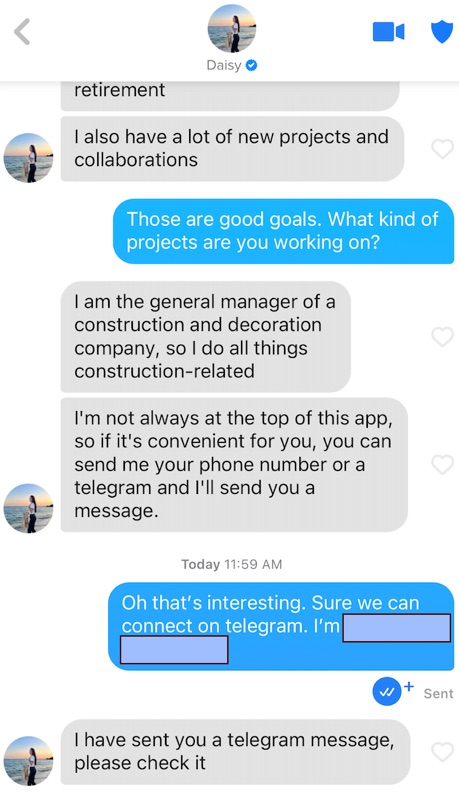
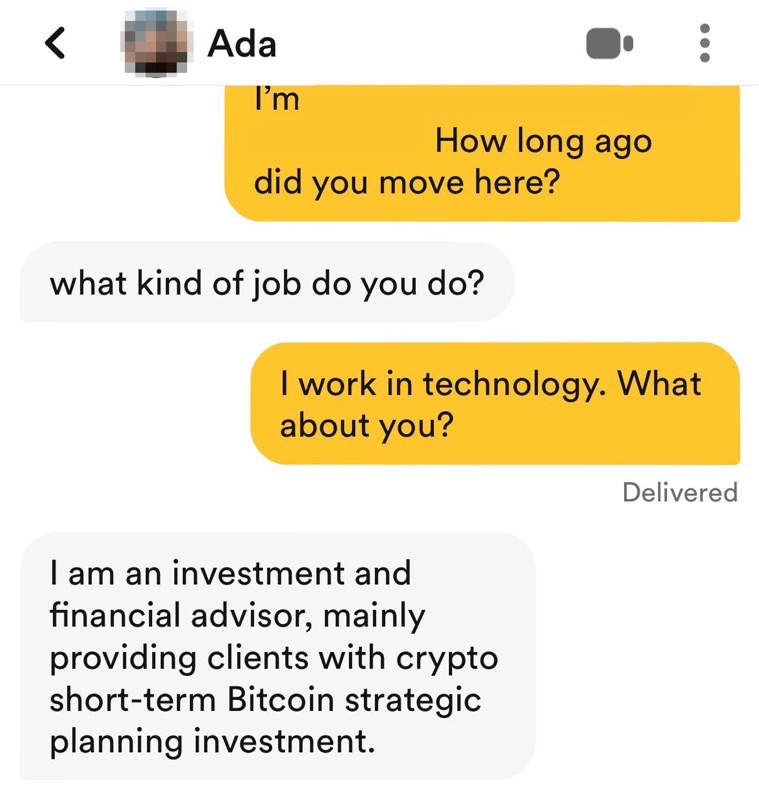
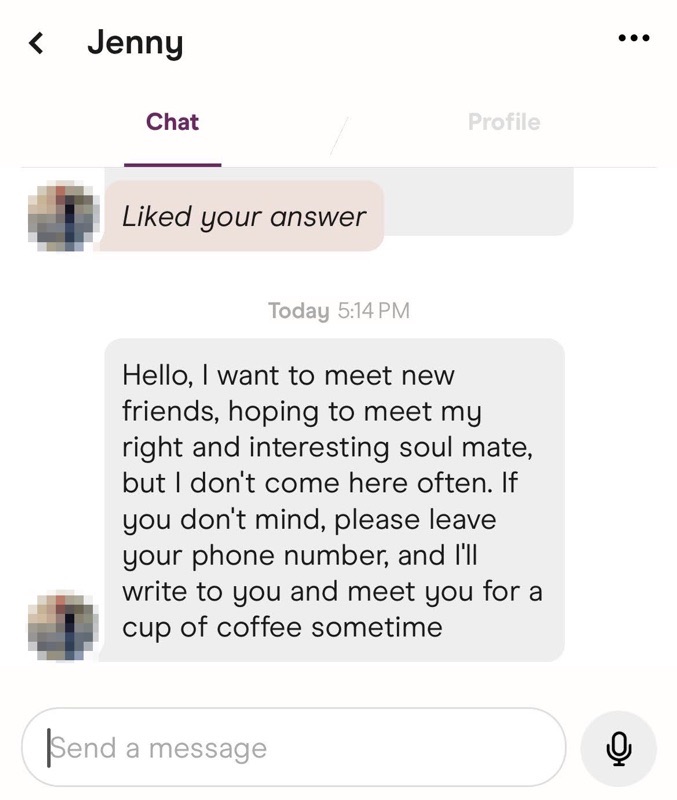
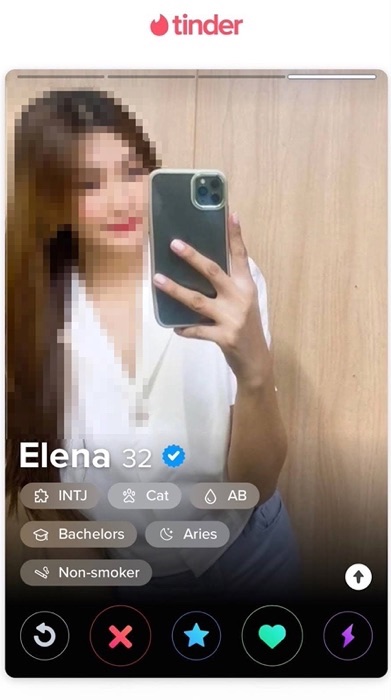
During my research, several of the Tinder profiles I encountered used highly unusual first names that didn’t make sense, like “Crush,” “Tomato” or “Mild.” There were also a number of profiles featuring identical names or duplicate photos. While some dating app users may choose to use a nickname or hide their real name, the consistency with which I encountered these unusual names coupled with their actions made it very clear these were fake profiles.


One other interesting element is that many of the pig butchering related Tinder profiles I encountered had the blue verified badge on their profile, a part of Tinder’s selfie verification process designed to serve as a safety feature for the platform’s users.
Why do pig butchers want to move off platform to WhatsApp, Telegram or SMS?
Pig butchers prefer to interact with potential victims via messaging services instead of on social media platforms for several reasons:
- Social media or dating platforms are highly populated and offer a wide pool of potential victims, so quickly shifting the interaction with a potential victim to another messaging service is an attempt to prevent these scam profiles from being reported and removed.
- Compared with social media platforms, messaging services have less moderation and weaker reporting functionality.
- Bogus social media profiles are meant to attract a steady stream of potential victims. However, once a victim bites, the social media platform isn't the ideal place to conduct the long con.
One thing is clear, the people operating these social media or dating app profiles are tasked with one job: move potential victims off platform quickly.
Are the same people behind both the social media and dating app profiles and the messaging apps?
No, I do not believe so. The accounts on social media and dating apps are designed to operate like what I call “herders.” They are different from the pig butchers, though they are all interconnected.
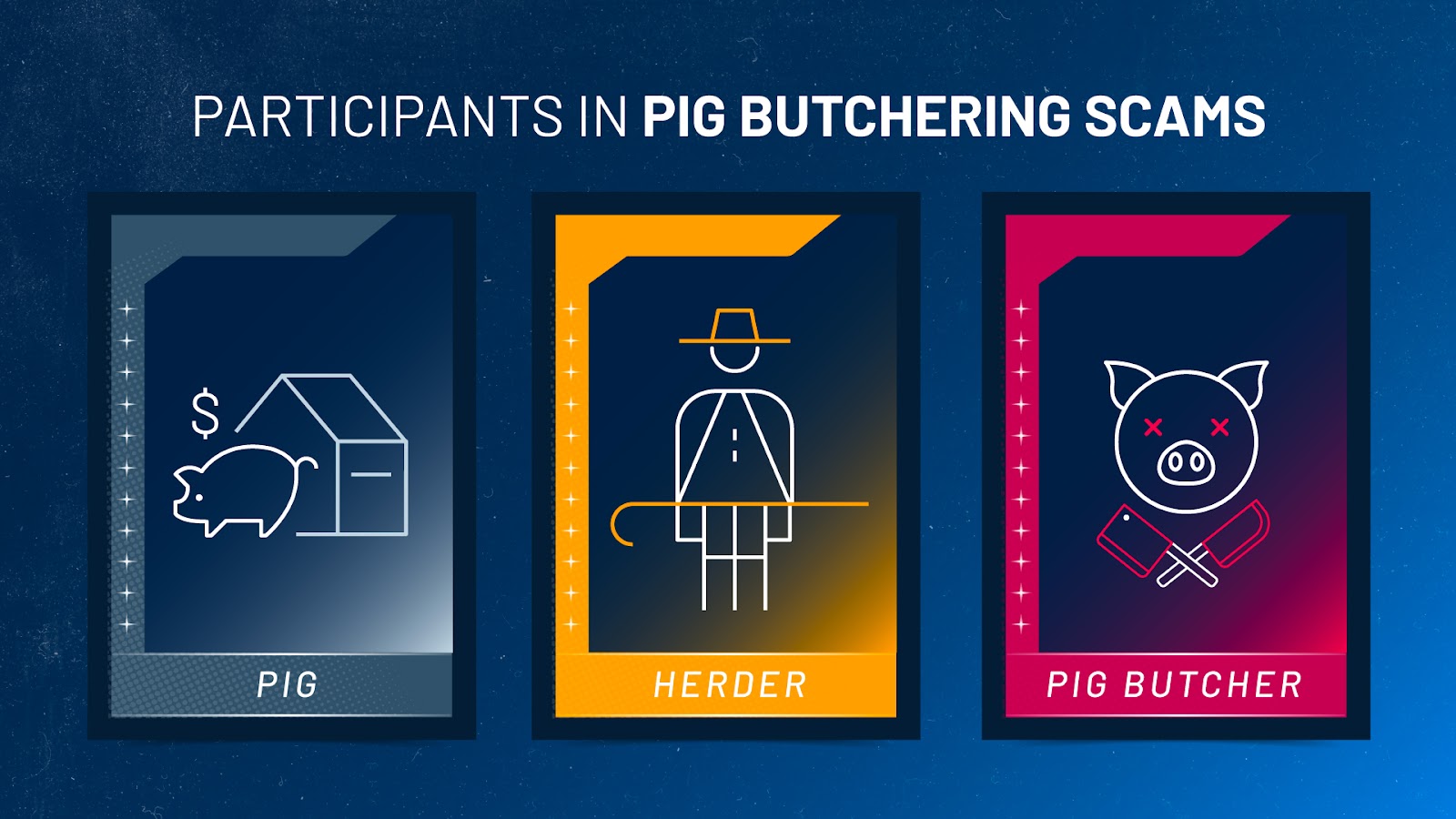
A herder is a person that is part of the pig butchering operation that is responsible for interfacing with large numbers of users daily on social media and dating applications, and their job is to simply convince as many “pigs” as possible to move off platform to messaging apps like WhatsApp, Telegram and SMS. Once the platform pivot happens, the rest of the communication is handled by pig butchers, who are people that are more seasoned at perpetrating the scams. The pig butcher is responsible for carrying out a prolonged conversation with a potential victim. This requires considerable finesse. If they try to strike too early, they risk losing out on stealing a significant sum of money from their victims.
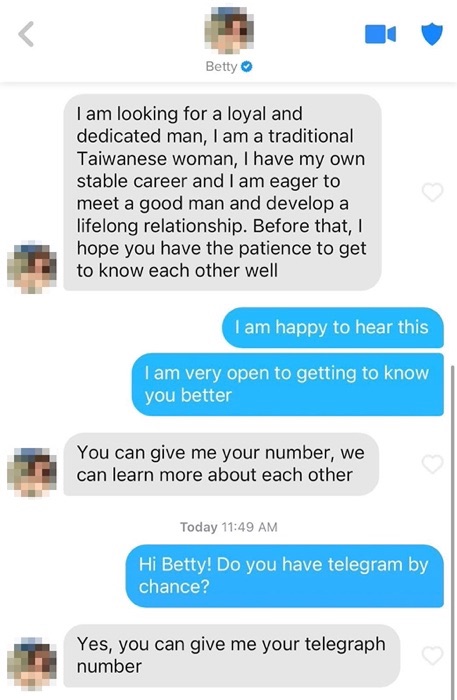
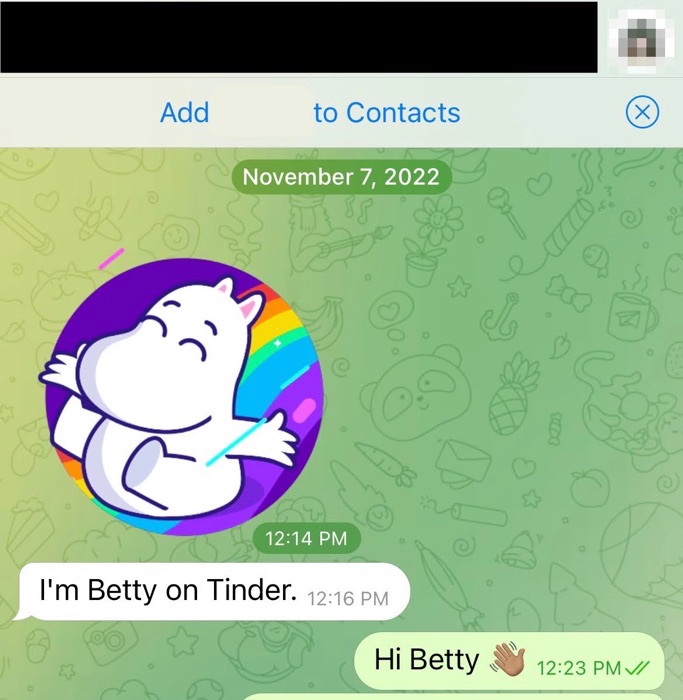
Example of a herder (left) and butcherer (right)
Reports suggest that pig butchers have a guide on how to conduct their conversations with victims. However, based on my experience in communicating with these pig butchers, I believe there are likely other individuals overseeing the operations, sort of like a supervisor would, in order to help the pig butchers respond to any tough questions that may pose a challenge.
Are all of the images on these social media and dating app profiles fake?
Yes, the images used as default pictures, avatars, profile photos and other photos shared on messaging platforms are all fakes and often stolen from legitimate users and repurposed for use in pig butchering scams.
But the person had a Facebook and Instagram account. Are those fake, too?
Yes, in some instances, the pig butchering scammers will create fake social media profiles to add legitimacy. Fake profiles on dating apps like Tinder often lack links to other social media platforms while legitimate users are more likely to include links to social profiles.
In the example above, “Betty” mentioned an Instagram profile in their Tinder bio. This led me to an Instagram account for “Betty” that also included a link to a Facebook profile for “Betty.”
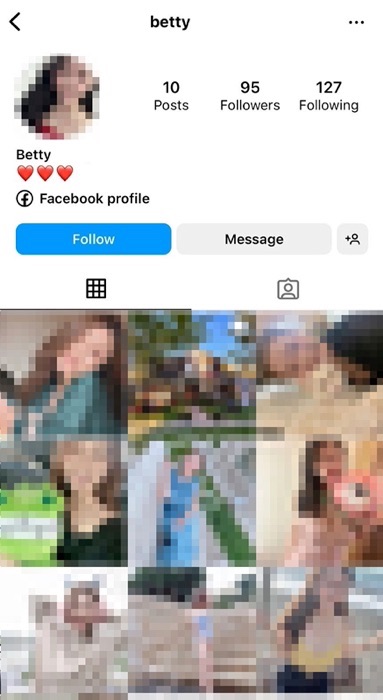
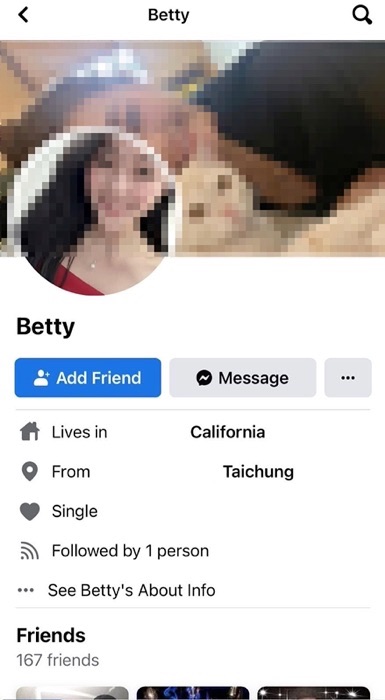
Ironically, the Facebook account for “Betty” asked in a post why some people are “so bored” and “likes [sic] to be a thief to steal people’s accounts” despite the fact that the profile for “Betty” was fake and using stolen photographs.

Have you seen artificial intelligence (AI) generated images used on these fake profiles?
I have encountered what I believe to be AI generated images used on dating app profiles instead of stolen photos.
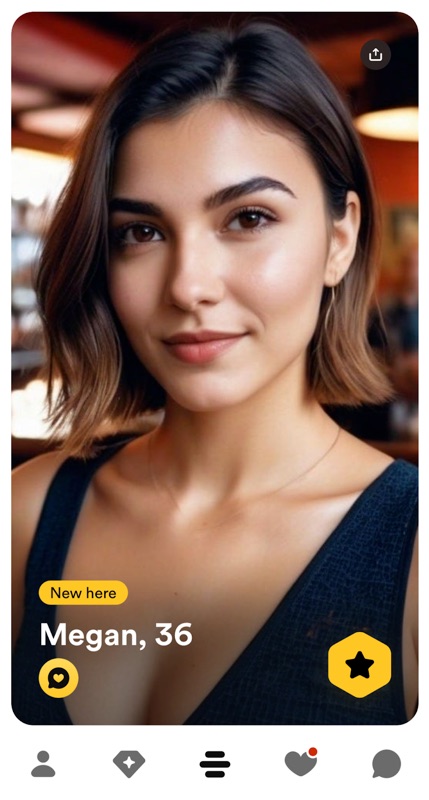
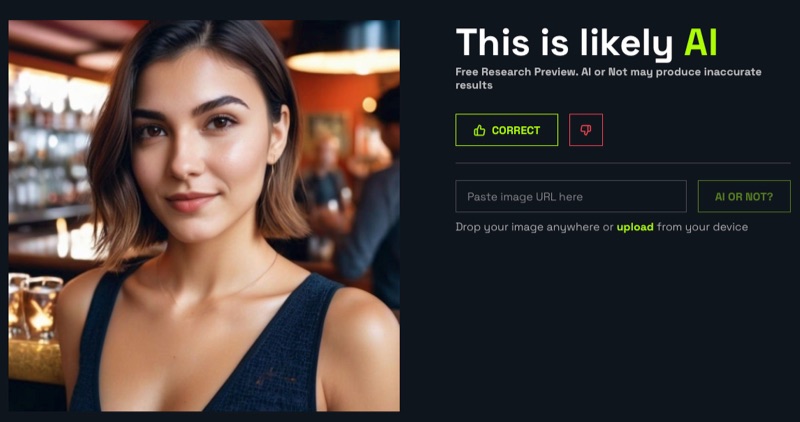
An example of a fake profile on Bumble using what appears to be an AI generated image and a result from AIorNot.com that flagged the profile photo as “likely AI”
However, I do not believe this phenomenon is widespread as of yet. Scammers creating pig butchering profiles on dating apps are still using stolen photographs to build these fake profiles, but we can anticipate that there will be a shift to more AI generated images and profile content crafted by large language model tools like ChatGPT, Google’s Gemini, and others.
Where are these pig butchering scammers based out of?
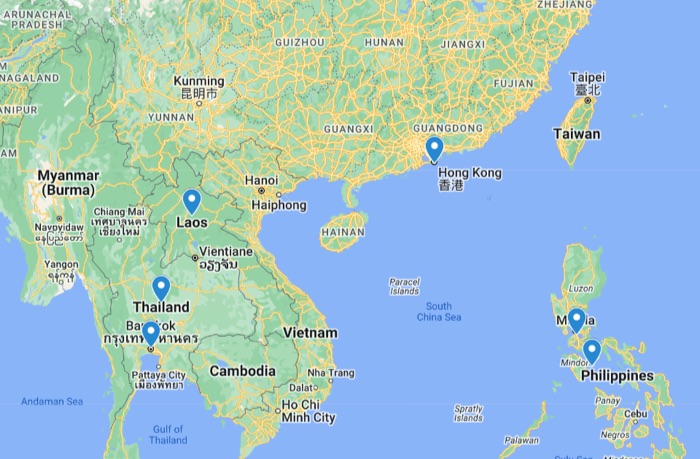
Based on my first-hand encounters with pig butchers, I was able to confirm that most of them are situated in Southeast Asian countries including but not limited to Thailand, Laos and the Philippines and the city of Hong Kong.
What is in the pig butcher's playbook?
Though unofficial, this has been my experience with the pig butcher’s playbook:
- Establish a foundation of regular communication
- Express care and interest in the potential victim
- Talk about their legitimate-sounding work and establish their knowledge of financial investments
- Brag about their savvy financial investment skills
- Convince the victim to invest fiat money or cryptocurrency
- Leave the victim empty handed
Let’s break down how each of the above steps plays out.
Establish a foundation of regular communication
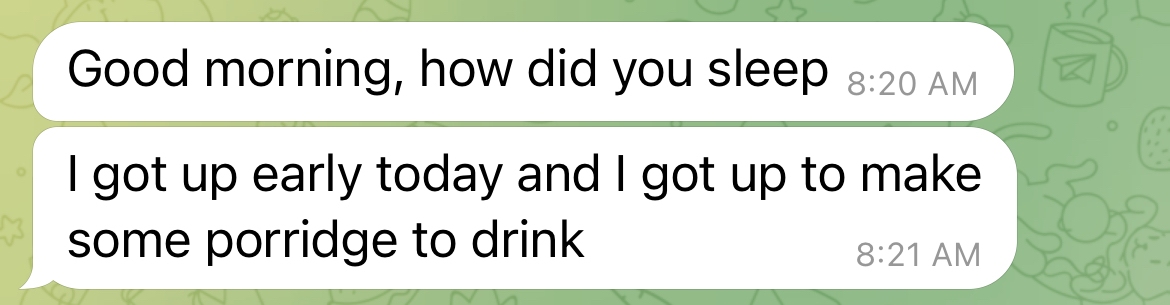
Pig butchers are in it for the long haul. The process is a long con requiring them to maintain a consistent level of communication with potential victims. They’ll send “good morning” and “good night” messages, tell victims about their fitness activities, share details about the work they’re allegedly doing and seek praise from the victim.

Express care and interest in the potential victim
Through my experiences, I’ve found that the primary way pig butchers express interest is through food. They will often ask if you’ve eaten breakfast, lunch or dinner. They will go out of their way to send you photos of their own meals. These tactics are, in my estimation, a way to establish care and concern for one's well being.
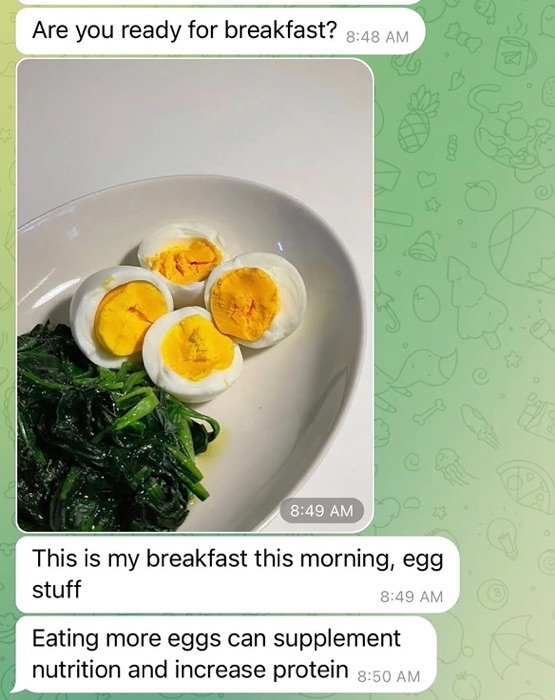
They will also talk about cooking for you or going out to eat together.
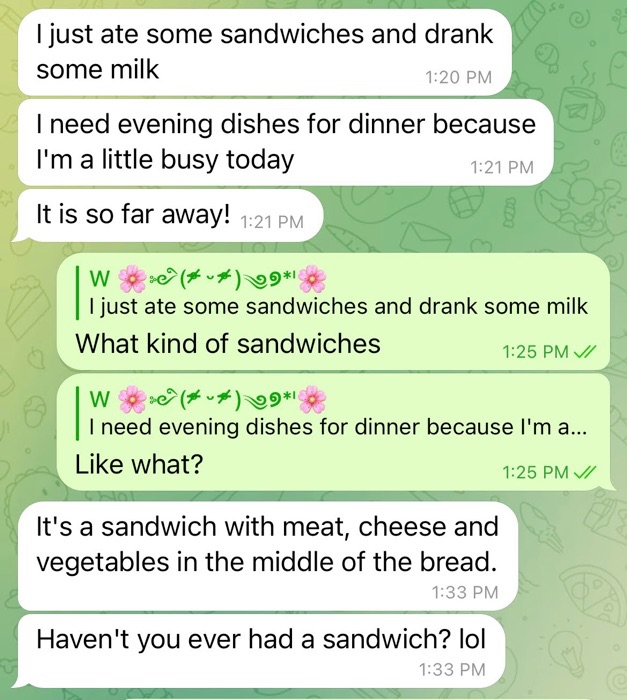
It’s clear that English is not the first language of many of the individuals operating the pig butchering accounts I’ve engaged with, as they’ve misinterpreted things and responded with shade, like asking me if I even know what a sandwich is.
In one instance, a scammer sent me voice memos and attempted to call me via the audio functionality of one application. I declined the call, but kept their voice memos. The following is a compilation of these clips stitched together:

Talk about their legitimate-sounding work and establish their knowledge of financial investments
Work is naturally a common talking point on dating apps. Pig butchers will invent stories about their fake personas’ day jobs and their financial success in real estate, the stock market or cryptocurrencies. They may frame the latter as “other financial products” as a way to avoid talking directly about cryptocurrencies at first.




They will ask you about your experience in investing in traditional finance (stocks, real estate) and alternative investments (cryptocurrency, spot gold).

Brag about their successful investment trades
They will share images of candlestick charts, which show price movement for a particular asset, whether it’s cryptocurrency like Bitcoin, Ethereum, or Litecoin; stablecoins like Tether; or successful trades involving spot gold like XAUUSD.
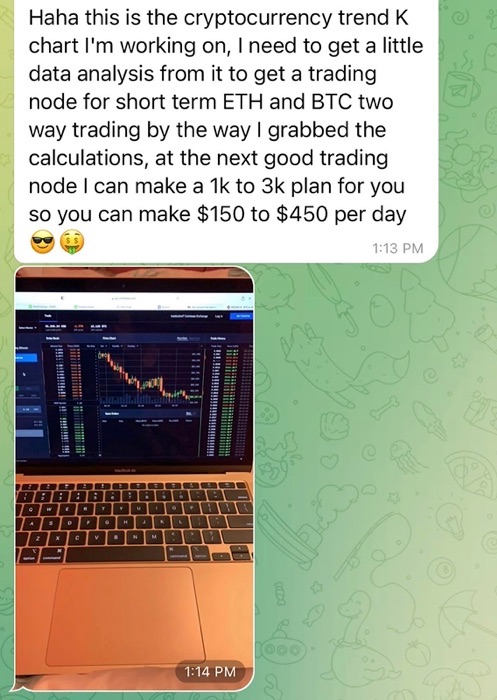
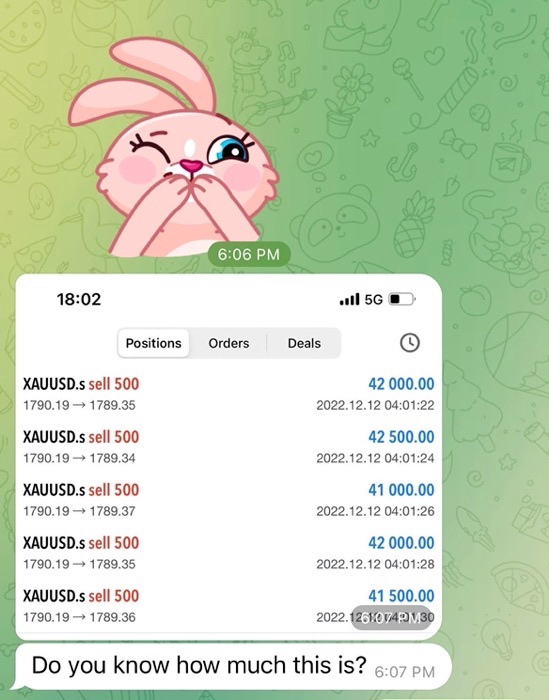
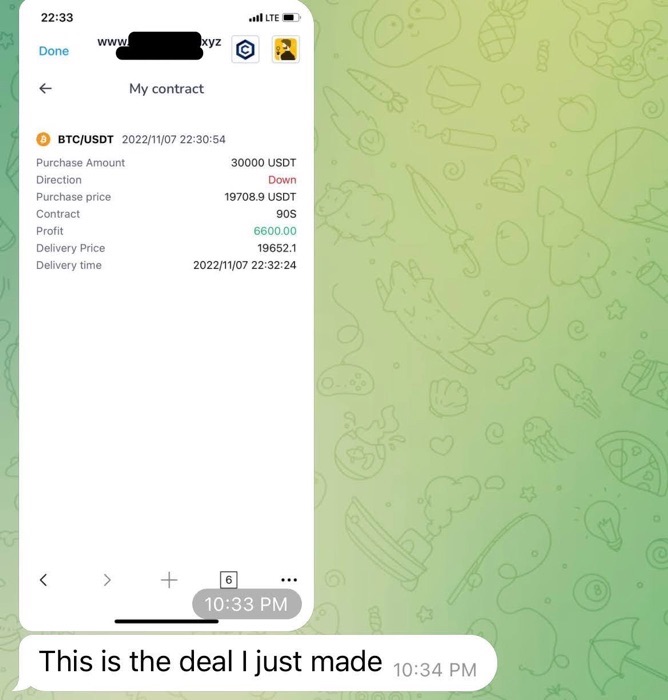
The pig butchers will offer to help teach you or guide you towards making profits.
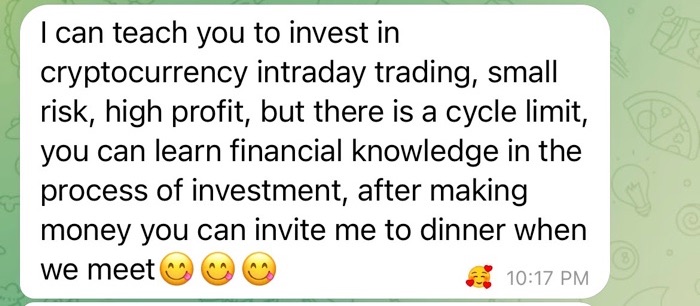
Many of the pig butchers I encountered often spun tales crediting their persona’s investment success to a parent, or another relative, such as an aunt or uncle. They may say these family members shared their guidance with them or that they have a professional investment team to help with their investment guidance.
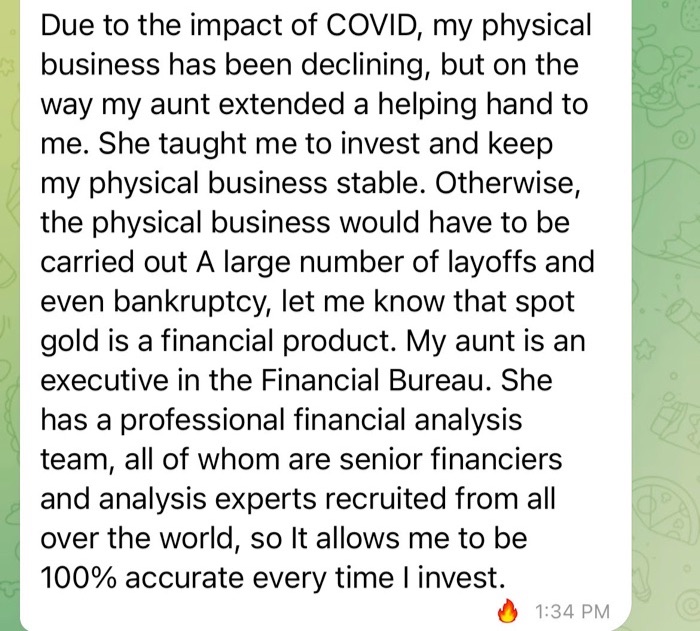

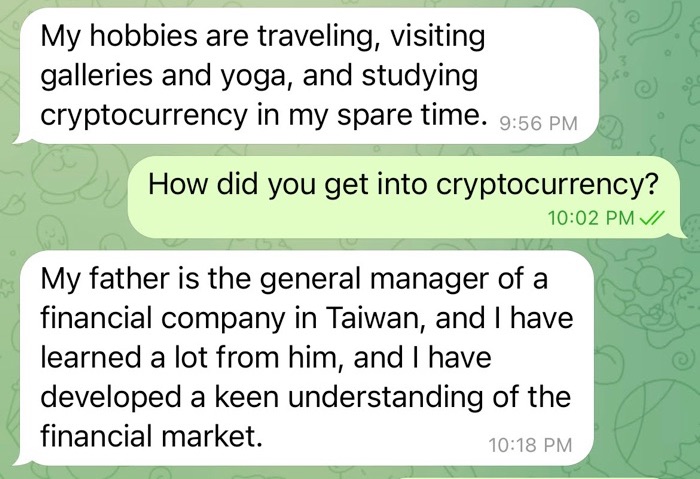
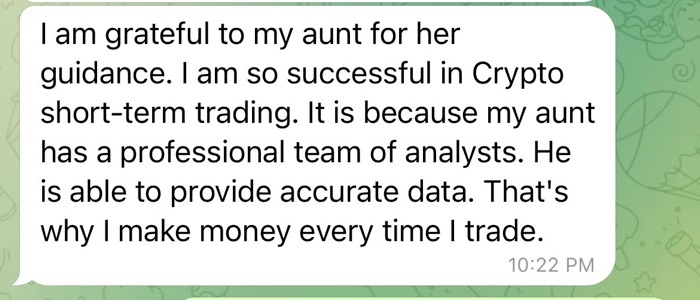
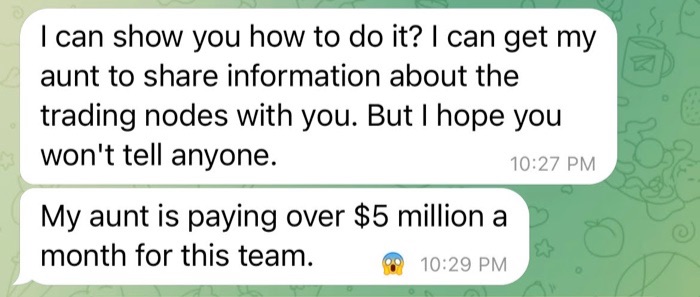
Before sharing investment guidance with you, the pig butchers may say that they need to seek permission from their mother, father, aunt or uncle. During this part of the conversation, you will typically be asked to keep this investment guidance a secret.
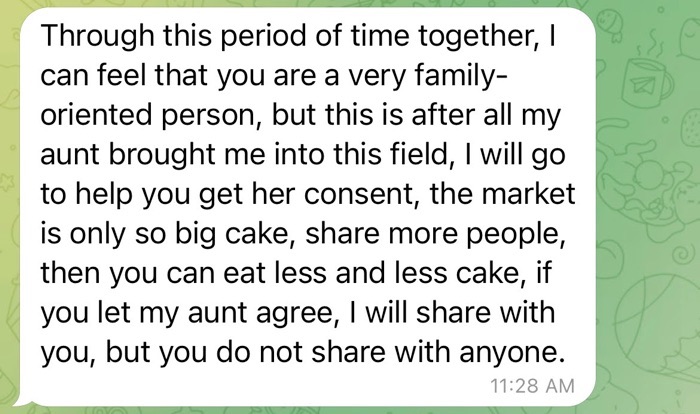
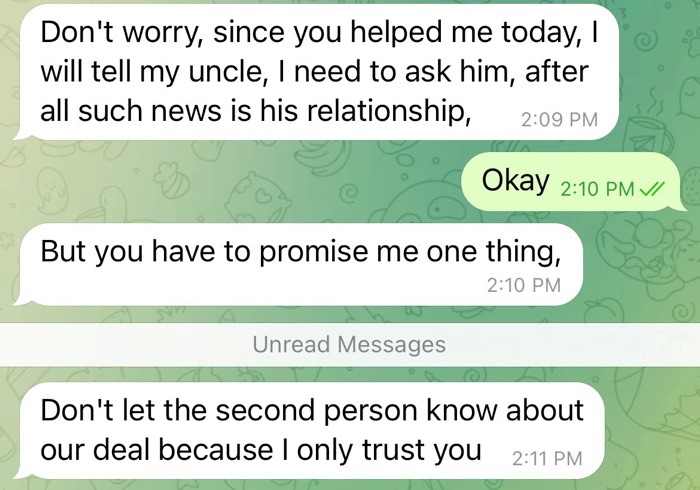

By framing this investment advice as secretive, the pig butchers are seeking to develop a type of intimacy with their victims that can be cashed in on later, once they try to convince them to invest their money.
Convince the victim to invest fiat money or cryptocurrency
The prolonged courtship conducted by pig butchers ultimately leads to asking their victim to invest fiat or cryptocurrency into one of several investment vehicles. These include cryptocurrency tokens, such as Bitcoin ($BTC), Ethereum ($ETH) and Litecoin ($LTC), or stablecoins like Tether ($USDT). They may also try to promote spot gold investments like $XAUUSD. These were the tokens I encountered during my research, though they do not represent an exhaustive list of tokens that may be shilled by these pig butchers.
For a more detailed look at the various investment instruments pig butchers use, please check out our second blog post.
Leave the victim empty-handed
The goal for the pig butchers is to steal as much money as possible from their victims. During my research, I did not reach this final stage. However, based on other accounts from victims, pig butchers may use tactics common to pyramid schemes and other investment scams, such as showing alleged profits to victims early on or even allowing them to withdraw some funds. This is part of the fattening-up process intended to further convince a victim that they are indeed making a profit. However, these so-called profits are most likely funds stolen from other victims that have been redistributed or have been presented as profits on spoofed investment sites controlled by the pig butchers. Ultimately, a pig butcher will ask a victim to invest more and more before leaving them high and dry.
In this blog post, I detailed how scammers behind pig butchering operations seek out their victims on messaging, social media and dating applications, how herders direct victims to more seasoned butchers and how a level of trust is established before the scam unfolds. In this series’ second part, I will explore how pig butchers leverage fake cryptocurrency investment sites and unofficial mobile applications to steal hundreds of millions of dollars from victims.
Learn more
Related Articles
- Research
- Exposure Management
- Research Reports




