Cybersecurity Snapshot: Latest MITRE ATT&CK Update Offers Security Insights on GenAI, Identity, Cloud and CI/CD

Check out what’s new in Version 15 of the MITRE ATT&CK knowledge base of adversary tactics, techniques and procedures. Plus, learn the latest details about the Change Healthcare breach, including the massive scope of the data exfiltration. In addition, why AI cyberthreats aren’t impacting CISOs’ budgets. And much more!
Dive into six things that are top of mind for the week ending April 26.
1 - New version of MITRE ATT&CK adds guidance on generative AI, cloud threats
Information about malicious use of generative AI tools. Advice about securing cloud environments. Recommendations for protecting software development pipelines. Those are just some of the new and updated areas included in the latest version of the widely used MITRE ATT&CK framework, announced this week.
“With v15 we were aiming for the perfect balance of familiar behaviors you’ve probably seen countless times … as well as newer, emerging trends,” reads the blog announcing Version 15 of MITRE ATT&CK, a knowledge base of adversary tactics, techniques and procedures.

Here’s some of what’s new:
- Insights into how hackers are leveraging generative AI tools, such as large language models (LLMs), to boost their cyberattacks
- Best practices for securing CI/CD pipelines, infrastructure as code (IaC) and cloud identity systems
- An explanation of how hackers have attacked enterprise IT systems as part of their efforts to breach industrial control systems (ICS)
- Information on new exploit techniques and mitigations for attacks targeting mobile devices
On related news, MITRE announced last week that one of its research and development networks was breached by a nation-state attacker that exploited the Ivanti Connect Secure zero-day vulnerabilities.
To get more details, check out:
- The announcement blog “ATT&CK v15 Brings the Action: Upgraded Detections, New Analytic Format, & Cross-Domain Adversary Insights”
- The release notes
- The detailed changelog
VIDEO
MITRE ATT&CK Framework (MITRE)
2 - Troves of personal data stolen in Change Healthcare breach
Hackers looted confidential health and personal information from a “substantial proportion” of Americans during the recent Change Healthcare breach, parent company United HealthGroup disclosed this week. But the full scope of the data theft won’t be known for a while.
“Given the ongoing nature and complexity of the data review, it is likely to take several months of continued analysis before enough information will be available to identify and notify impacted customers and individuals,” the statement reads.
United HealthGroup also acknowledged that a sampling of the stolen data was leaked online in the dark web as screenshots. According to media reports, the data was leaked by extortion group RansomHub to pressure United HealthGroup into meeting their payment demands.

The company also admitted in a statement sent to the media that it paid a ransom “to do all it could to protect patient data from disclosure.”
It didn’t specify to which cybercrime group it made the payment, but ransomware gang BlackCat / Alphv carried out the original breach, which snarled Change Healthcare’s systems for over a month. The attack caused a major, nationwide disruption for patients, hospitals, doctors and pharmacies in areas such as billing, payments processing, patient care and prescription fulfillment.
Citing anonymous sources, the Wall Street Journal reported this week that the attackers gained entry into Change Healthcare’s network in mid-February after compromising the credentials of a remote-access application that wasn’t protected by multi-factor authentication.
And for those of you tracking the financial impact of the massive breach, United last week disclosed the breach’s current and projected costs: about $870 million in the recently-concluded first quarter, and up to $1.6 billion by year’s end.
The breach was characterized as “the most significant and consequential incident of its kind against the U.S. healthcare system in history” by Rick Pollack, President and CEO of the American Hospital Association.
For more information about the Change Healthcare breach:
- “Hackers Broke Into Change Healthcare’s Systems Days Before Cyberattack” (WSJ)
- “Authentication failure blamed for Change Healthcare ransomware attack” (CSO)
- “A large US health care tech company was hacked. It’s leading to billing delays and security concerns” (Associated Press)
- “Why UnitedHealth, Change Healthcare were targeted by ransomware hackers, and more cybercrime will hit patients, doctors” (CNBC)
VIDEO
Tenable CEO Amit Yoran Discusses Ransomware Attack on UnitedHealthcare on CNN
3 - CISA, FBI: How to prevent foreign cyber tampering of U.S. elections
With the U.S. general election just months away, U.S. intelligence and law enforcement agencies are taking steps to protect the electoral process and infrastructure from cyberattacks, including the malicious use of artificial intelligence (AI) to generate misinformation.
To that end, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the FBI and the Office of the Director of National Intelligence (ODNI) have published a guide for election teams that details cyberattack tactics and mitigations.

“We are putting out this guide because our strategy in combating this threat starts with awareness and collaboration. We will continue to relentlessly pursue bad actors looking to disrupt our election infrastructure,” Joseph Rothrock, Acting Assistant Director of the FBI's Counterintelligence Division, said in a statement.
Titled “Securing Election Infrastructure Against the Tactics of Foreign Malign Influence Operations,” the eight-page document identifies the governments of China, Russia and Iran as the primary nation-state attackers trying to use cyberattacks to interfere with and disrupt the upcoming U.S. elections.
Malicious tactics include:
- Voice-cloning of public figures
- Theft of confidential information from target organizations
- Fabricating evidence about alleged security incidents
- Use of social media to spread misinformation
These are some of the cyber agencies’ mitigation recommendations for election officials and their staffs:
- Proactively debunk misinformation by directing the public to legitimate, official and trusted sources of information.
- Craft incident response plans to detail how your staff should respond to misinformation campaigns.
- Secure your social media accounts by using the strongest security and privacy controls available and by deactivating dormant, unused profiles.
- Protect email and other digital accounts with multi-factor authentication.
- Watermark your content to indicate it is legitimate.
For more information about protecting the electoral process from cyberattacks:
- “From deepfakes to social engineering, here's what to know about elections, cybersecurity and AI” (World Economic Forum)
- “Can We Protect the Ballot Box? Global Guide to Election Cyber Threats in 2024” (Infosecurity Magazine)
- “Cyber chiefs confident 2024 election will be ‘most secure’ in history” (Politico)
- “New tech to fuel more sophisticated, prevalent election cyber threats” (SC Magazine)
4 - Survey: AI cyberthreat not yet altering CISOs’ plans
While CISOs recognize the heightened risk from malicious use of AI, they’re not changing their priorities or budgets accordingly.
That’s the main takeaway from a ClubCISO survey of cybersecurity leaders from public- and private-sector organizations.
“Among the myriad risks vying for the CISO’s attention, AI cyber-attacks are not yet forcing a change of focus,” reads an announcement of the ClubCISO report.

Key findings include:
- 63% of respondents rate the severity of AI cyberattacks as “critical” or “high” and believe they’ll be “extremely damaging” to businesses.
- 62% say the industry isn’t prepared to deal with the AI cyberthreat.
- 77% say AI cyberattacks haven't prompted them to modify their cybersecurity spending.
- A small minority are hiring staff skilled at recognizing AI cyberattacks (6%) or at defending against them (7%).
For more information about the report, check out the announcement “AI cyber-attacks a critical threat, but CISO priorities are not changing yet” from ClubCISO, which is backed by Australian tech services provider Telstra Purple.
For more information about what CISOs need to know about AI:
- “AI security for CISOs: A dynamic and practical framework” (Security Magazine)
- “The CISO’s Guide to Generative AI” (Deloitte)
- “Navigating AI: What are the top concerns of Chief Information Security Officers?” (World Economic Forum)
- “CISO Planning for 2024 May Struggle When It Comes to AI” (Dark Reading)
- “The CISO's Guide to AI: Embracing Innovation While Mitigating Risk” (SANS Institute)
5 - A check on cloud security practices, apropos of the AWS FlowFixation vulnerability
During our recent webinar about the AWS FlowFixation vulnerability that was recently discovered by Tenable Research, we polled attendees about a few cloud security issues. Check out what they said about their awareness of their public cloud instances and about their public cloud usage.
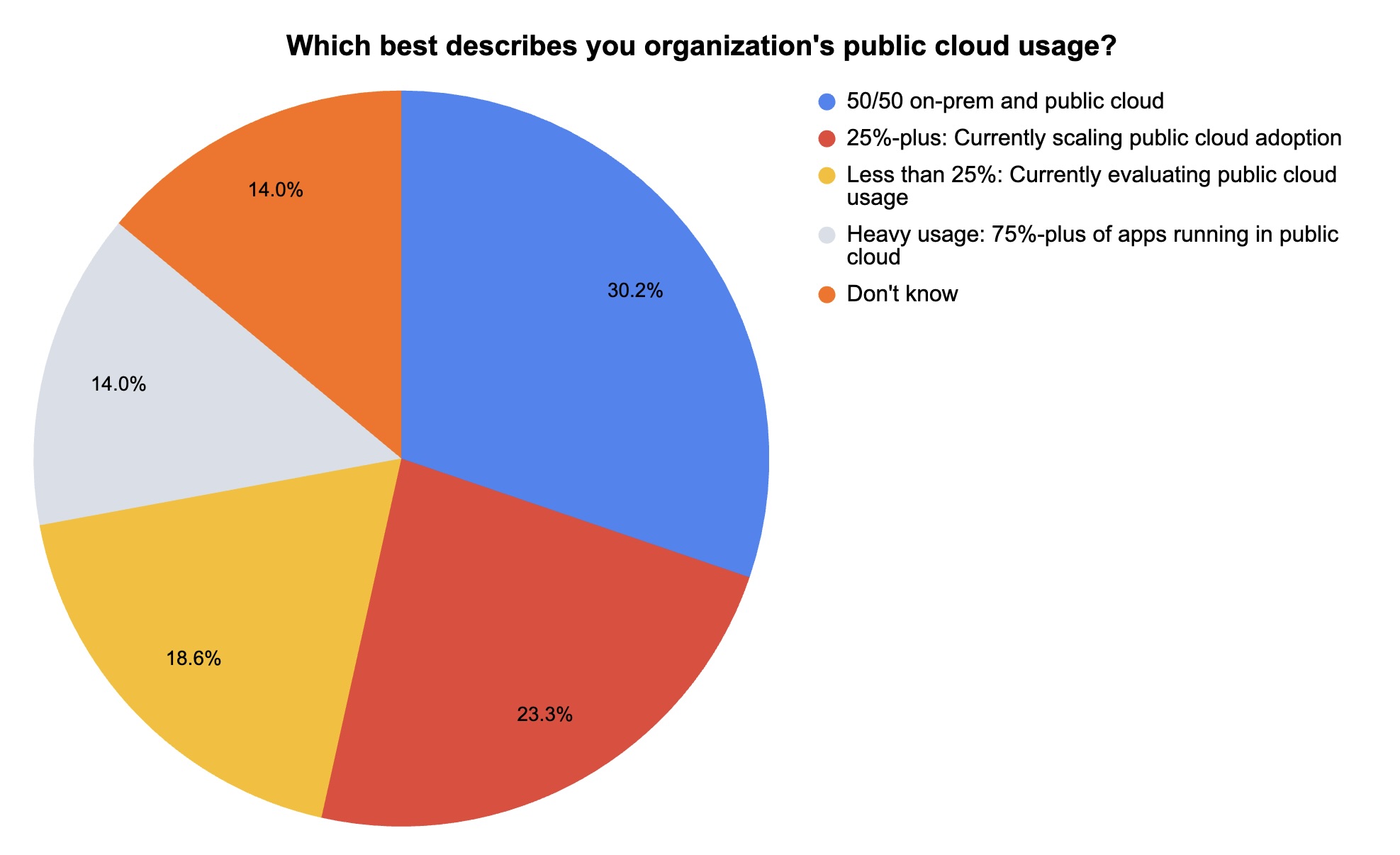
(43 webinar attendees polled by Tenable, April 2024)
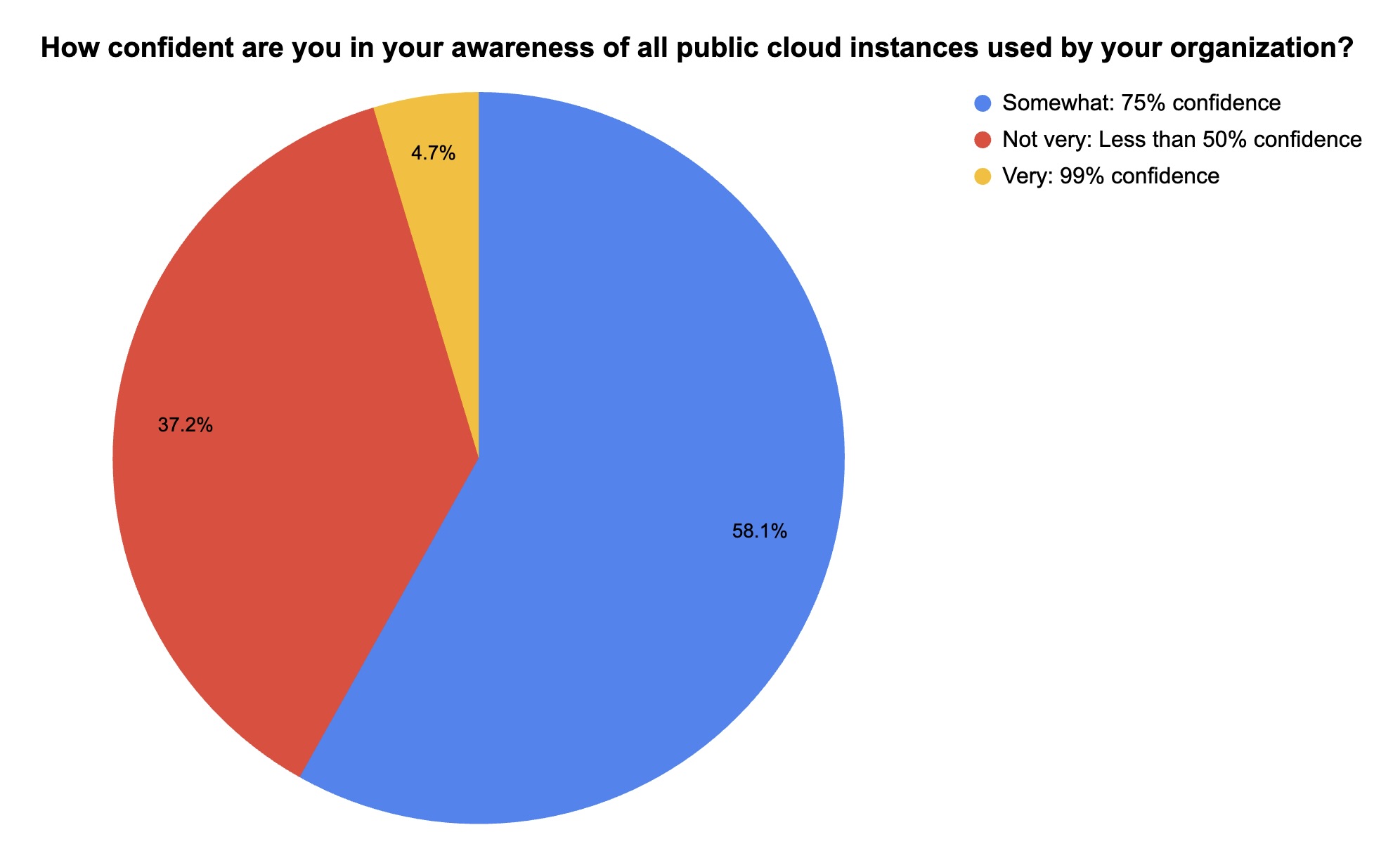
(43 webinar attendees polled by Tenable, April 2024)
Want to learn more about the AWS Flow Fixation vulnerability discovery and how you can take preventative action and strengthen your cloud security posture? Watch the on-demand webinar “What the AWS FlowFixation Vulnerability Reveals About the Way Your Team Practices Preventive Security and What To Do About It Now.”
Topics covered include:
- Achieving complete visibility across all your organization’s public domains
- Incorporating web scan data with cloud assessment results to find critical flaws and toxic combinations
- How a unified approach to governing cloud configurations and access controls eliminates critical blind spots
6 - FTC: Impersonation scams surge, helped by digital communications
U.S. consumers lost $1.1 billion last year to scammers who impersonated either a business or a government agency – an increase of more than 300% compared with 2020.
That’s according to the U.S. Federal Trade Commission’s (FTC) “Impersonation scams: not what they used to be” report.
Unsurprisingly, the use of digital communications tools to carry out these impersonation scams is rising fast. Specifically, fraudsters are using email and text messages much more frequently than in the past, while the use of phone calls is trending down.
Impersonation Scammers' Changing Contact Methods
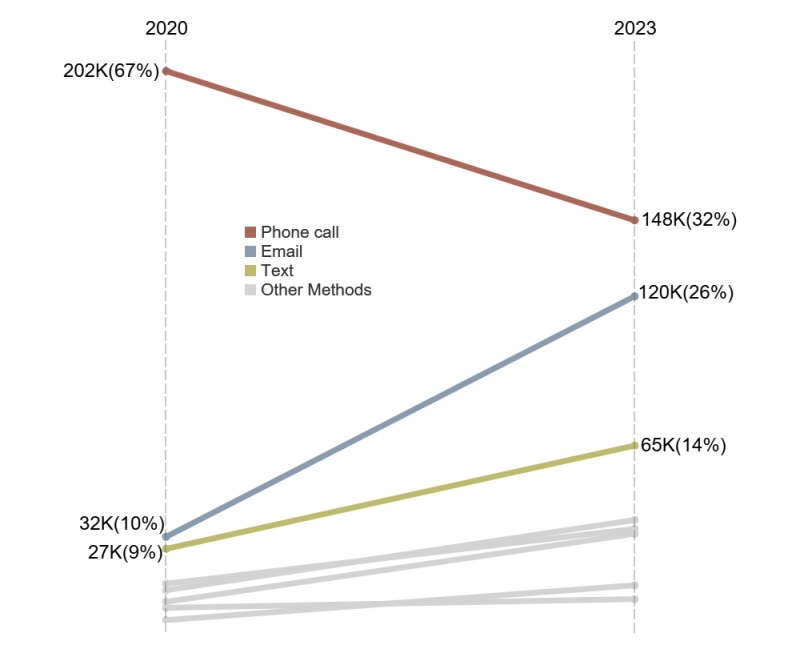
(Source: U.S. Federal Trade Commission’s “Impersonation scams: not what they used to be” report, April 2024)
The FTC recorded 330,000-plus reports of business impersonation scams and almost 160,000 reports of government impersonation scams last year.
Related Articles
- Cloud
- Exposure Management
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Healthcare
- Internet of Things
- Risk-based Vulnerability Management





