Tenable CIEM
Cloud Infrastructure and Entitlement Management

In the public cloud, identities and entitlements are the greatest risk to your cloud infrastructure. A single identity and access management (IAM) misconfiguration can give bad actors access to your entire cloud environment. Tenable CIEM addresses these challenges, enabling you to implement a least-privilege model and scale adoption of cloud in a secure way.
Request a Demo
CIEM - The Essential Next Step in Your Cloud Security Strategy
Identities are part of almost all data breaches. Bad actors are targeting mismanaged IAM privileges to access your sensitive data. Ironically, almost all cloud permissions are over-privileged — an accident waiting to happen. Cloud complexity — including 1,000s of microservices needing access to resources and layers of policies that often change — makes understanding access risk and permissions difficult.
Leading analysts call on enterprises to automate entitlement management and least privilege as a key part of a cloud strategy. CIEM enables you to do so.
Data Sheet: Cloud Infrastructure and Entitlement Management
Get Industry-Leading Cloud Identities and Entitlements Security with Tenable
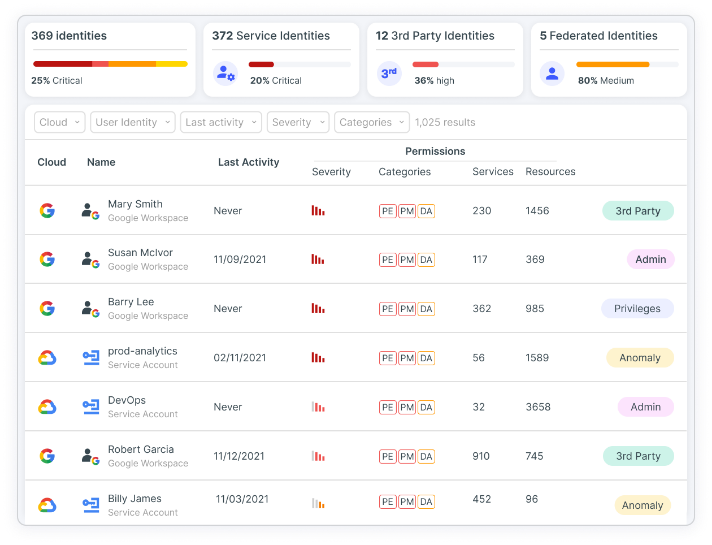
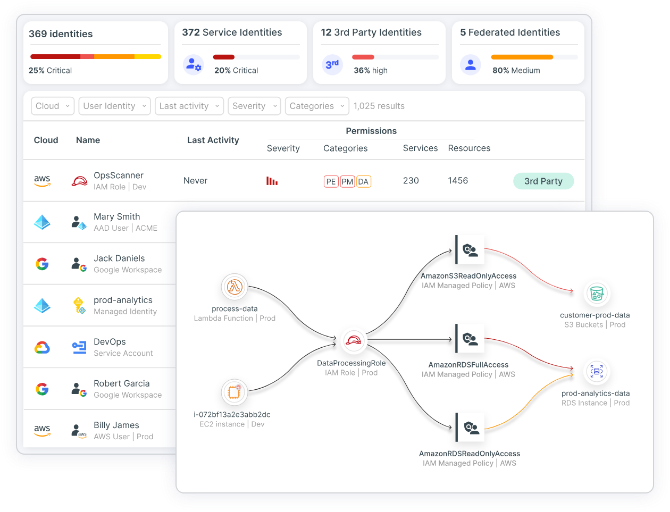
Tenable CIEM offers the most comprehensive solution for managing human and service identities in cloud infrastructure. The solution lets you visualize all identities and entitlements, using automated analysis to reveal and prioritize risks, including excessive permissions and toxic combinations, accurately and in context. Using Tenable CIEM to manage your cloud identities, you gain fine-grained insight into the access needed to perform a task, remediate risk using automated workflows, shift left on least privilege and investigate suspicious behavior.
With Tenable CIEM, you can answer your most critical identity-related cloud security questions:
- Who has access to which resources in the cloud?
- Where are my greatest risks?
- What do I need to do to remediate?
- How do I ensure compliance in the cloud?
White Paper: Why Managing Cloud Entitlements is Nearly Impossible
“Ermetic [now Tenable Cloud Security] goes beyond permissions visibility to reveal IAM risk context that informs our busy DevOps team, facilitating their efforts in mitigating risk and minimizing disruption.”Guy Reiner, Co-founder and VP of R&D, Aidoc
Multi-Cloud Asset Management and Full-Stack Risk Assessment
With Tenable CIEM, you can continuously discover and visualize a full inventory of all cloud identities, entitlements, resources and configurations in your cloud environment, including IAM, federated and third-party users. It applies full-stack analysis that evaluates cloud provider permission models across identity, network, compute and data resources to surface precise findings in context. Using Tenable CIEM, you get comprehensive insight into identity-related risk, including excessive permissions, network exposure and hidden dangers.
Blog: 3 Cloud IAM Security Questions You Must Be Able to Answer
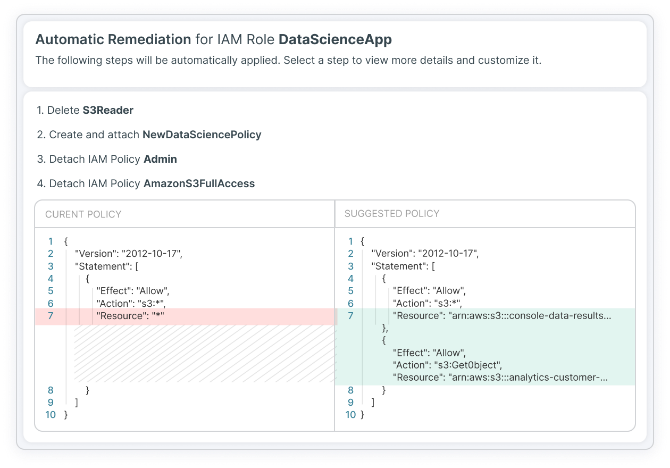
Automated Remediation Customized to Your Needs
Tenable CIEM helps mitigate risky privileges — and faulty configurations — through automated and assisted remediation tools. Using Tenable CIEM, you can rapidly drop unintended entitlements and misconfigurations and the threats they pose.
- Leverage wizards that display remediation steps and choose to auto-remediate
- Insert auto-generated optimized policies and configuration fixes into existing DevOps workflows such as Jira or ServiceNow
- Lower mean time to remediate (MTTR) by delivering right-sized, least-privilege code snippets to developers
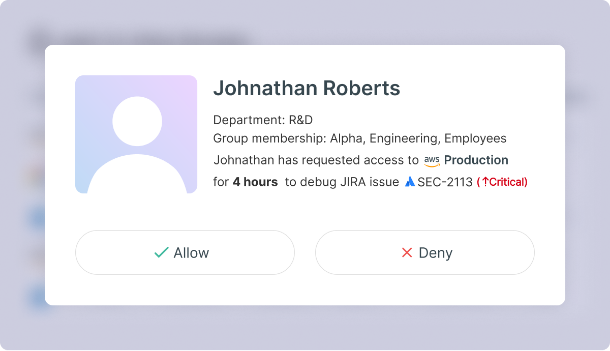
Enable Innovation Without Sacrificing Security With Just-in-Time (JIT) Access
Your engineering teams sometimes need highly privileged access to sensitive cloud environments, such as for debugging or manual deployment of a service. Broad access can introduce risk if not revoked when no longer needed. Tenable Just-in-Time (JIT) access management lets you control developer access based on business justification. Using Tenable JIT you can enforce fine-grained least-privilege policies and avoid long-standing privileges, minimizing your cloud attack surface. You can enable developers to quickly submit requests, notify approvers and gain temporary access. You can maintain governance by tracking activity during the session and generating detailed JIT access reports.
Webinar: JIT Privileged Access Management for Cloud Infrastructure
Investigate Threats and Detect Anomalies
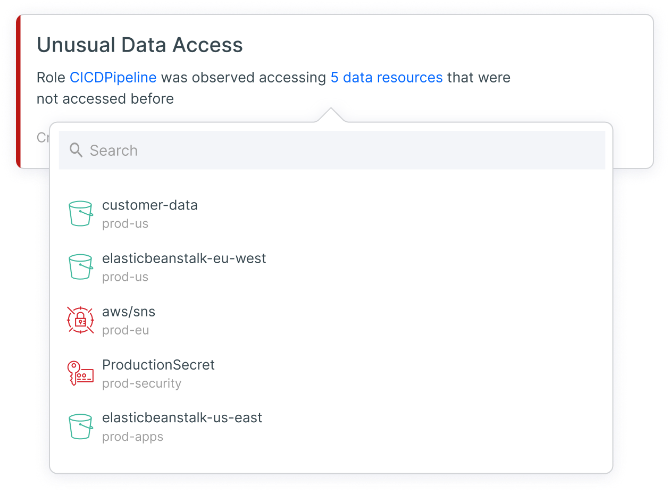
With Tenable CIEM, you can perform continuous cloud risk analysis against behavioral baselines to detect anomalies and suspicious activity. Tenable CIEM identifies identity-based threats such as unusual activity related to data access, network access management, permission management, privilege escalation and more. By querying enriched logs, you can understand, view and investigate risks in context. You can further lower MTTR through integrations with SIEM solutions (such as Splunk and IBM QRadar) and with ticketing/notification systems (such as ServiceNow and Jira).
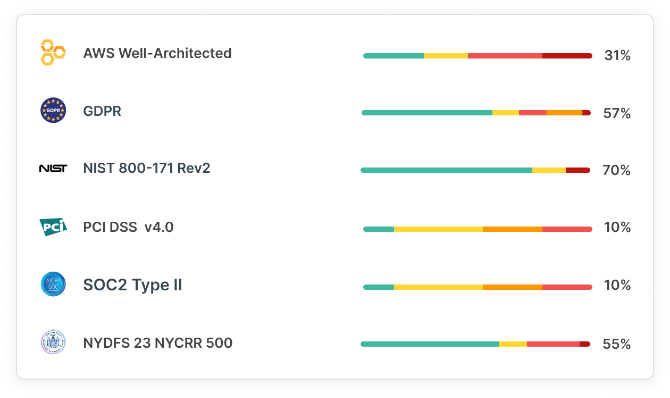
Continuous Access Governance and Compliance
Security and privacy regulations (e.g., CIS, SOC2, HIPAA) require organizations to have cloud security capabilities for governing access policy and enforcing least privilege. These controls enable continuous auditing and automated reporting on how you use privileged cloud identities. Your pathway to least privilege and shift-left starts with a full and accurate picture of all entitlements. Tenable CIEM uses analysis to auto-generate access policies based on actual needs that integrate into your remediation workflows. You gain valuable tools for continuously checking compliance and the ability to easily produce detailed reports.
Learn More: CSPM Solutions
Tenable Cloud Security - A Unified CNAPP
Tenable offers a comprehensive cloud-native application protection platform (CNAPP) for AWS, Azure and GCP as Tenable Cloud Security. With market-leading cloud infrastructure entitlement management (CIEM) at the core, it dramatically reduces your cloud attack surface and enforces least privilege at scale.