Tenable OT Security
OT and ICS Cyber Risk Management: Complete Visibility, Security and Compliance
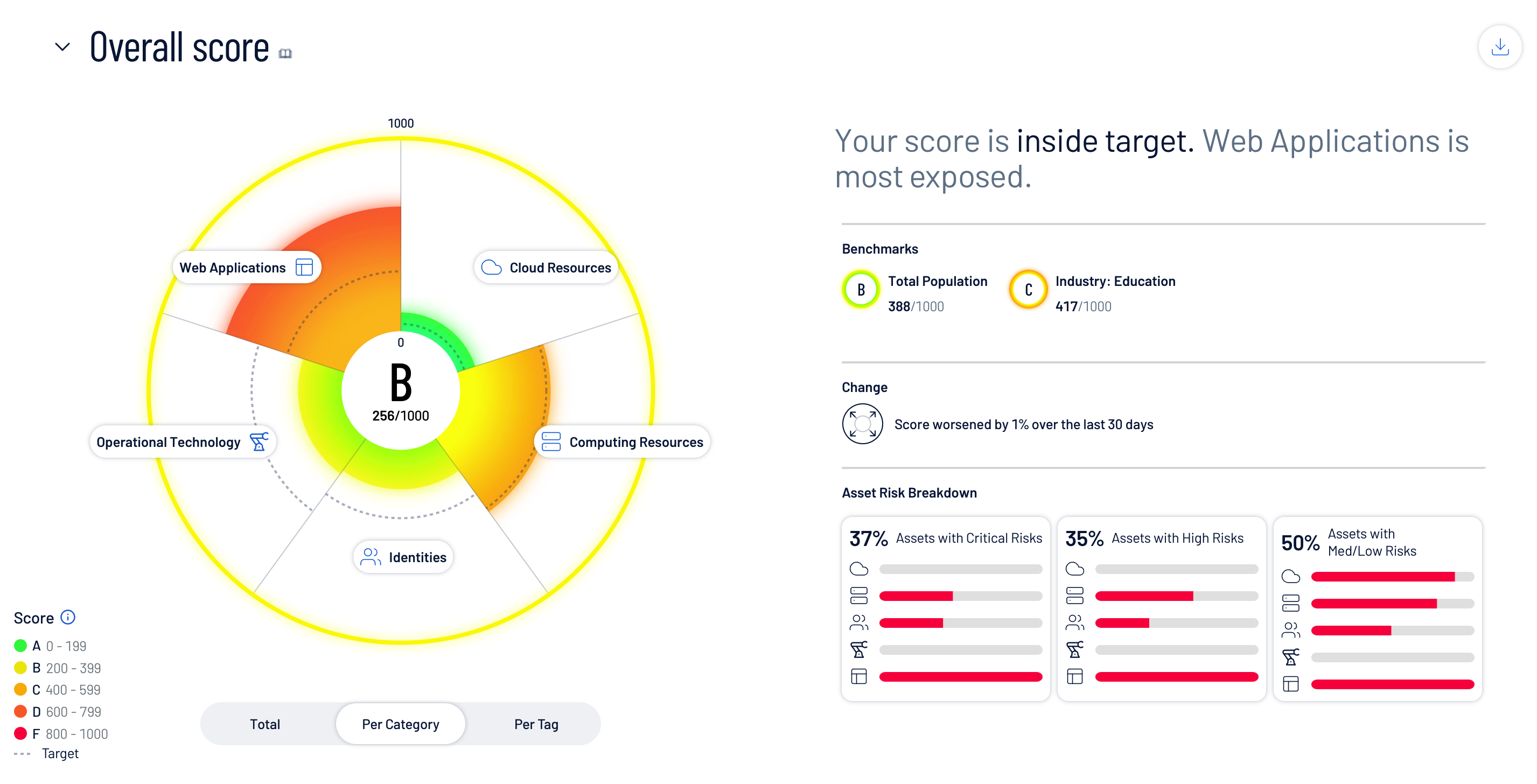
Get in-depth operational technology (OT) asset visibility to better understand, manage and reduce your cyber risk. Tenable OT Security (formerly Tenable.ot) is an industrial security solution for your modern industrial enterprise. It can help you identify assets in your OT environment, communicate risk, prioritize action and enable your IT and OT security teams to work better together.
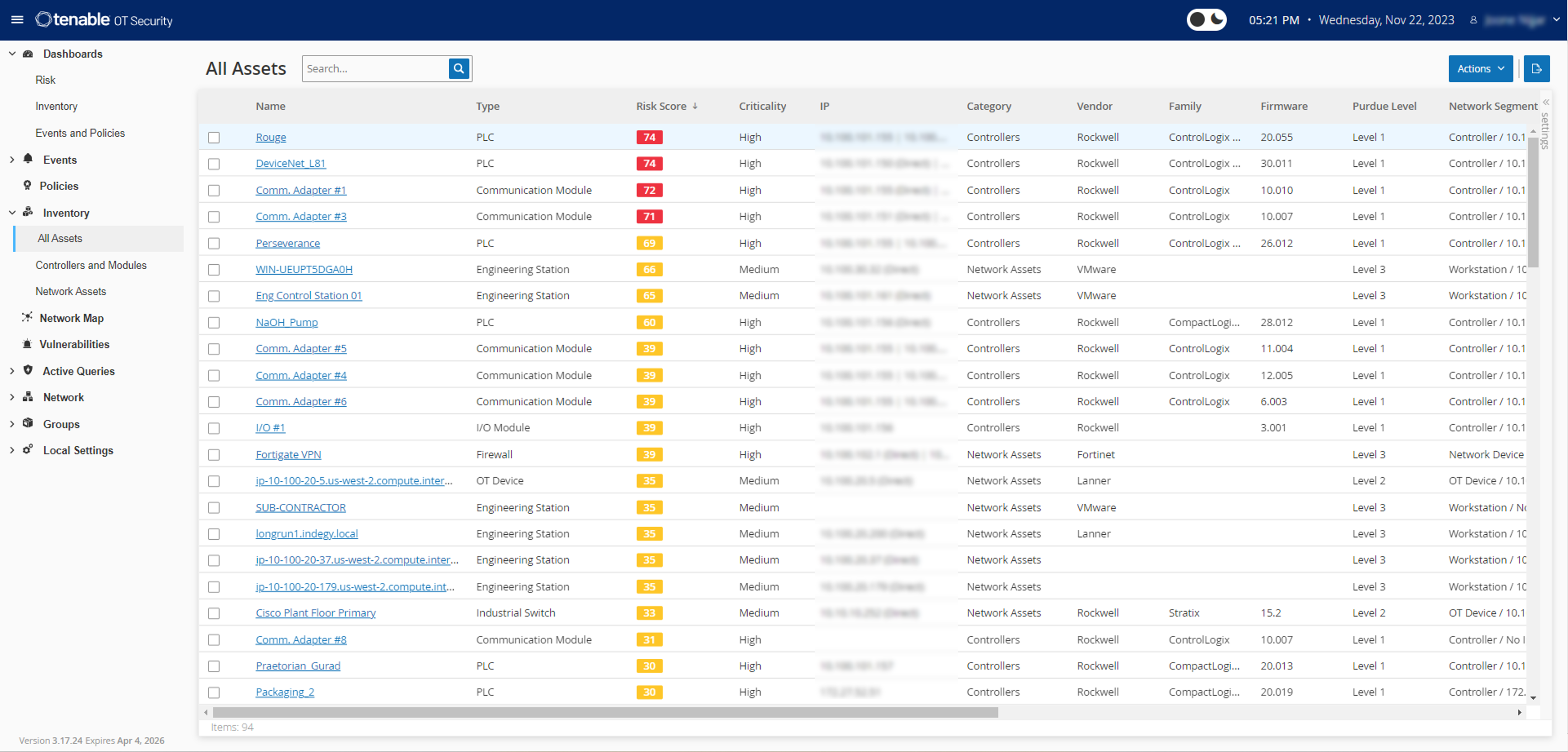
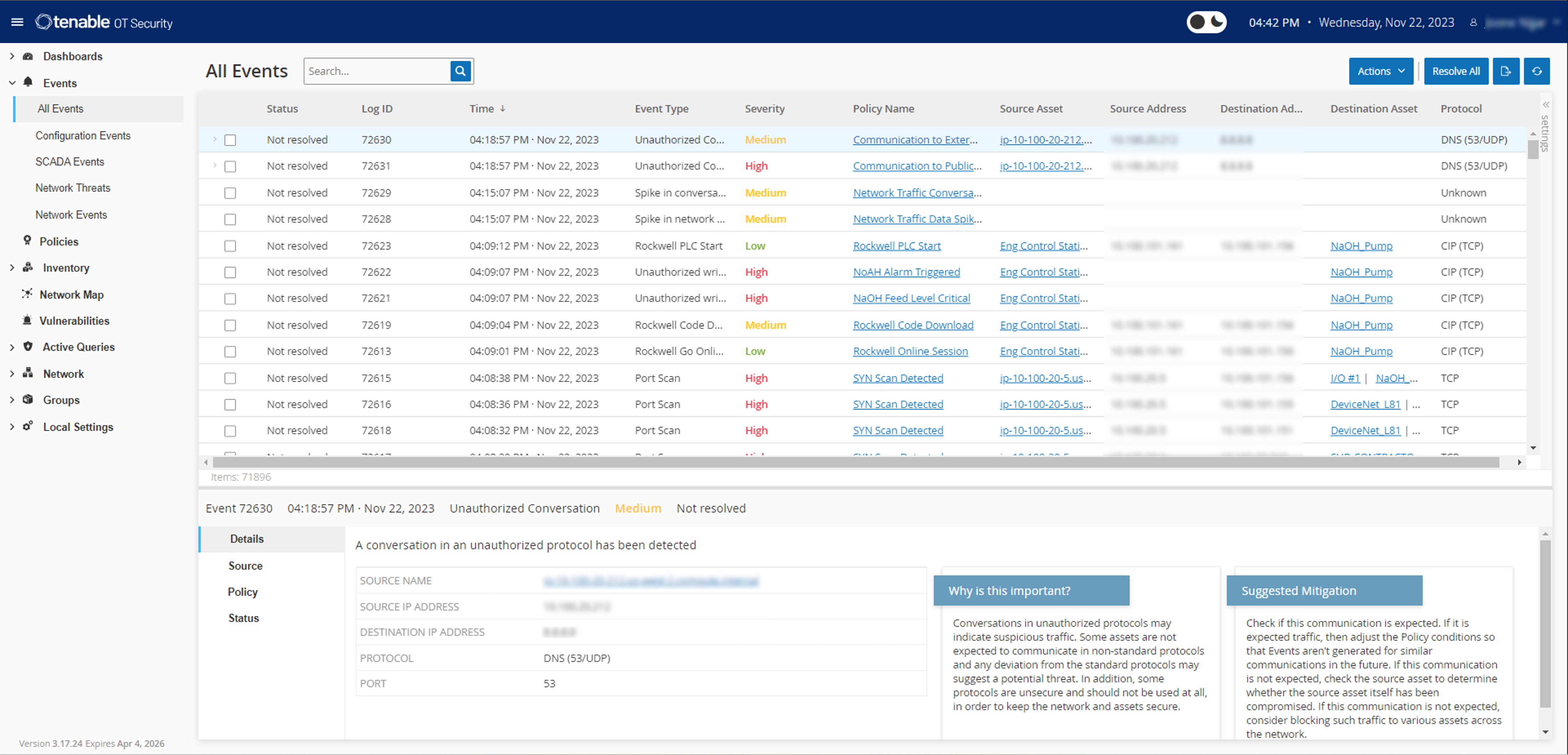
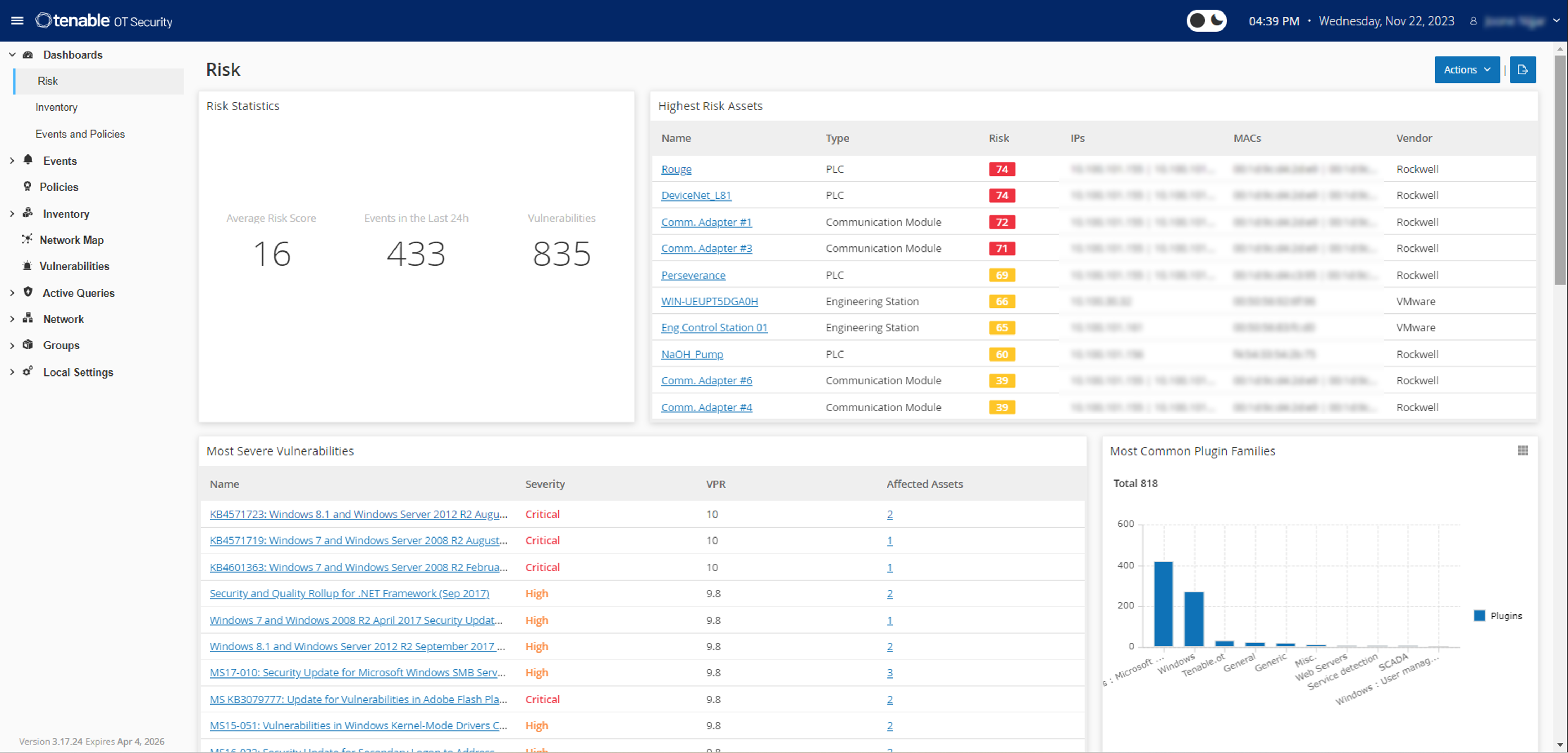
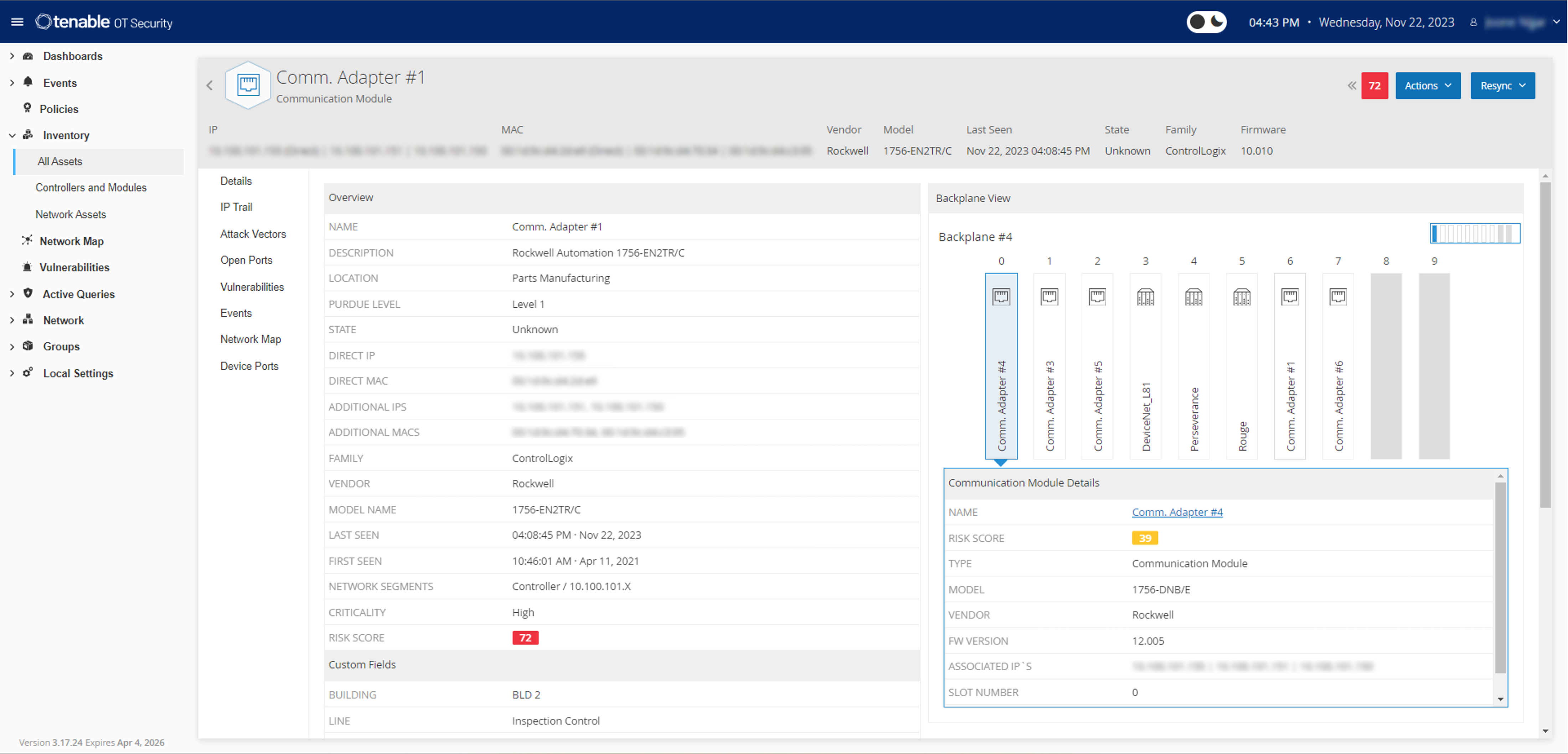
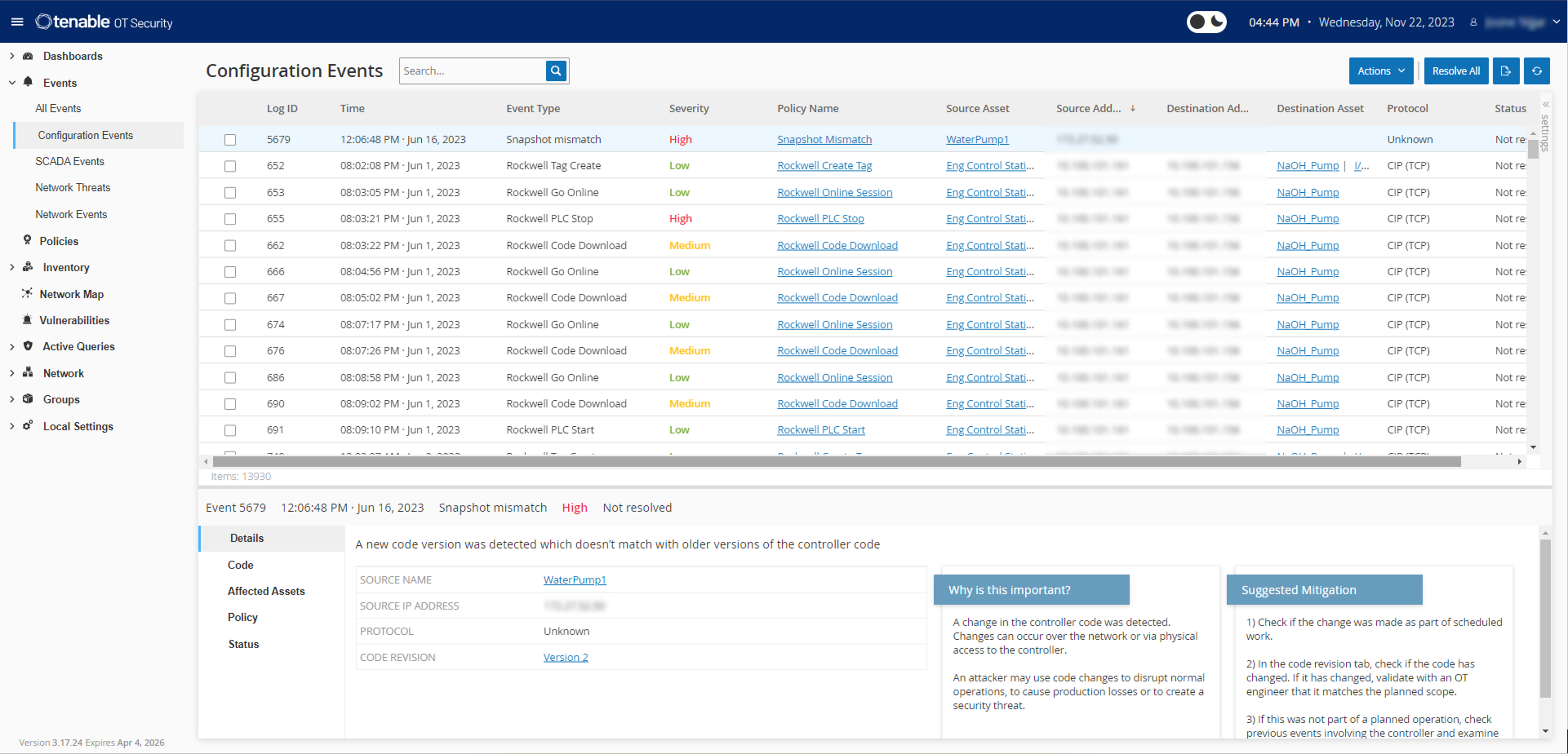
With a comprehensive set of security tools and reports, Tenable OT Security provides unmatched visibility across IT and OT security operations and delivers deep situational awareness across all global sites and their respective assets — from Windows servers to PLC backplanes — in a single interface.
Comprehensively Reduce your OT Cyber Risk with Tenable OT Security
Up to 50% of your OT infrastructure contains IT assets. Attacks can easily propagate across IT/OT infrastructure.
Complete visibility and security for every asset across the extended cyber attack surface: IT, OT, and IoT assets.
- Comprehensive visibility beyond the IT environment to the modern attack surface
- Risk intelligence to mitigate operational risks
- Actionable planning and decision making across the modern enterprise
A Leader in OT
Security Solutions
Secure your OT/ICS environment with a recognized industry leader
Trusted by Customers Worldwide
"We chose Tenable OT Security for its unique ability to monitor, proactively detect and alert our staff to any changes made to our industrial control systems that could impact their integrity and proper operation."Steve Worley
Tenable OT Security 3-Minute Explainer Videos
Tenable OT Security protects your industrial networks from cyber threats, malicious insiders and human error. It identifies and protects OT environments from cyber risk and threats and ensures operational safety and reliability.
As a cybersecurity leader, what if you could give your cybersecurity team the power to operate like a team three or four times its size? Tenable OT Security helps teams operate more efficiently by reducing the time it takes to identify and detect, and more quickly remediate vulnerabilities across the rapidly expanding attack surface.Dr. Michael Mylrea