- Exposure Management
- Tenable Vulnerability Management
- Tenable Security Center
- Tenable Security Center Plus
- Tenable Nessus
How mature are your cyber defender strategies?
Tenable Research analyzed more than 300,000 real-world vulnerability assessments from 2,100 organizations.
What we learned will transform how you think about cyber hygiene.
Download the Free ReportCyber Defender Strategies Report
What Your Vulnerability Assessment Practices Reveal
What’s your vulnerability assessment style? Are you scanning weekly, monthly or quarterly? And, what does your scanning habit reveal about the maturity of your organization’s vulnerability assessment practices, a critical part of cyber hygiene?

These are the key questions Tenable Research set out to answer in our Cyber Defender Strategies Report. We discovered four common vulnerability assessment strategies in use today. These strategies tell us how mature an organization’s vulnerability discovery process is – and help us identify ways to improve.
Download the report now to:
- Learn what the four vulnerability assessment styles tell us about cyber risk maturity.
- Compare your vulnerability assessment strategy to these four common scanning styles.
- Find out what steps you can take today to improve your vulnerability assessment strategy – no matter where you are on the maturity scale.
Download the Report:
Cyber Defender Strategies Report
What we learned about enterprise cyber risk maturity
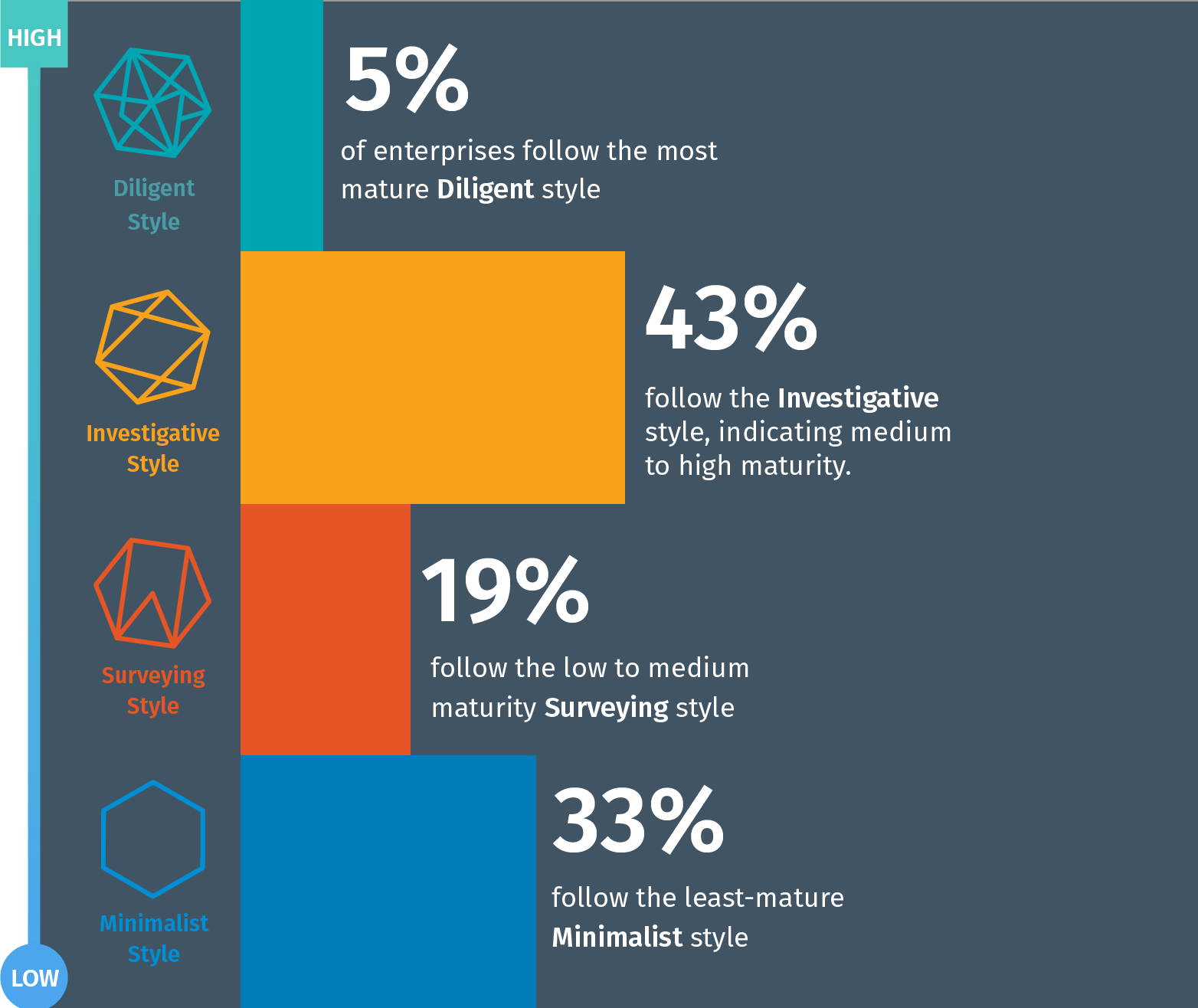
For our Cyber Defender Strategies Report, we analyzed key performance indicators (KPIs) based on real-world vulnerability assessment behavior. These KPIs correlate to four VA maturity styles: Diligent, Investigative, Surveying and Minimalist.
We discovered about half (48%) of the enterprises included in the data set are practicing very mature (Diligent or Investigative) styles in their vulnerability assessment strategies. However, just over half (52%) exhibit moderate- to low-level vulnerability assessment maturity (practicing a Surveying or Minimalist style).
Our Cyber Defender Strategies Report provides recommendations for each VA style, to help you advance to the next maturity level. We also explore how these four VA styles are distributed across major industry verticals and by organization size, so you can compare yourself with your peers.
Cyber Risk Maturity Scale